Attack Simulator in Office 365 – aanval simulatie uitvoeren
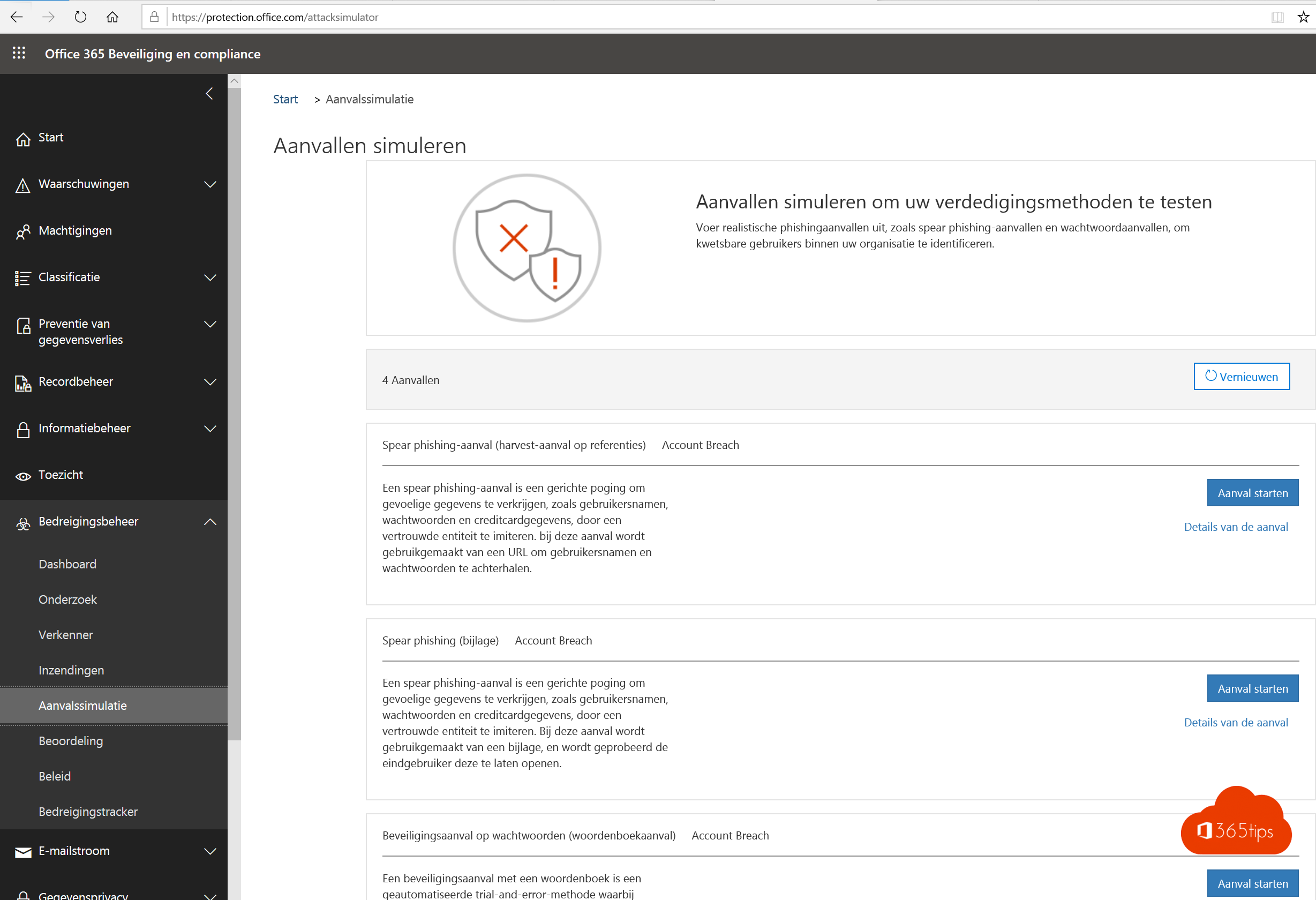
Aanvalssimulator uitvoeren om weerstand rond Multi-factor authentication aan te pakken
Weerstand om MFA uit te rollen in je organisatie? Eerder gaf ik al concrete tips om MFA in te schakelen of Security Defaults.
In deze blog geef ik concreet advies om te staven waarom je als organisatie beter kiest voor MFA. Met onderstaande stappen heb je een duidelijk overzicht van de risico’s die je loopt als je geen gebruik maakt van Multi-factor Authentication.
Rapporteren
Het is vaak de rol van de IT-organisatie om steeds de risico’s te kunnen faciliteren en te rapporteren. Uiteraard met actuele cijfers, deze bekom je via een test met de attack-simulator.
Het is een organisatie verantwoordelijkheid om te handelen naar de risico’s van de organisatie. Breng de risico’s in kaart en leg deze risico’s vast zodat de trends kunnen geanalyseerd worden, en de nodige acties uitgevoerd.
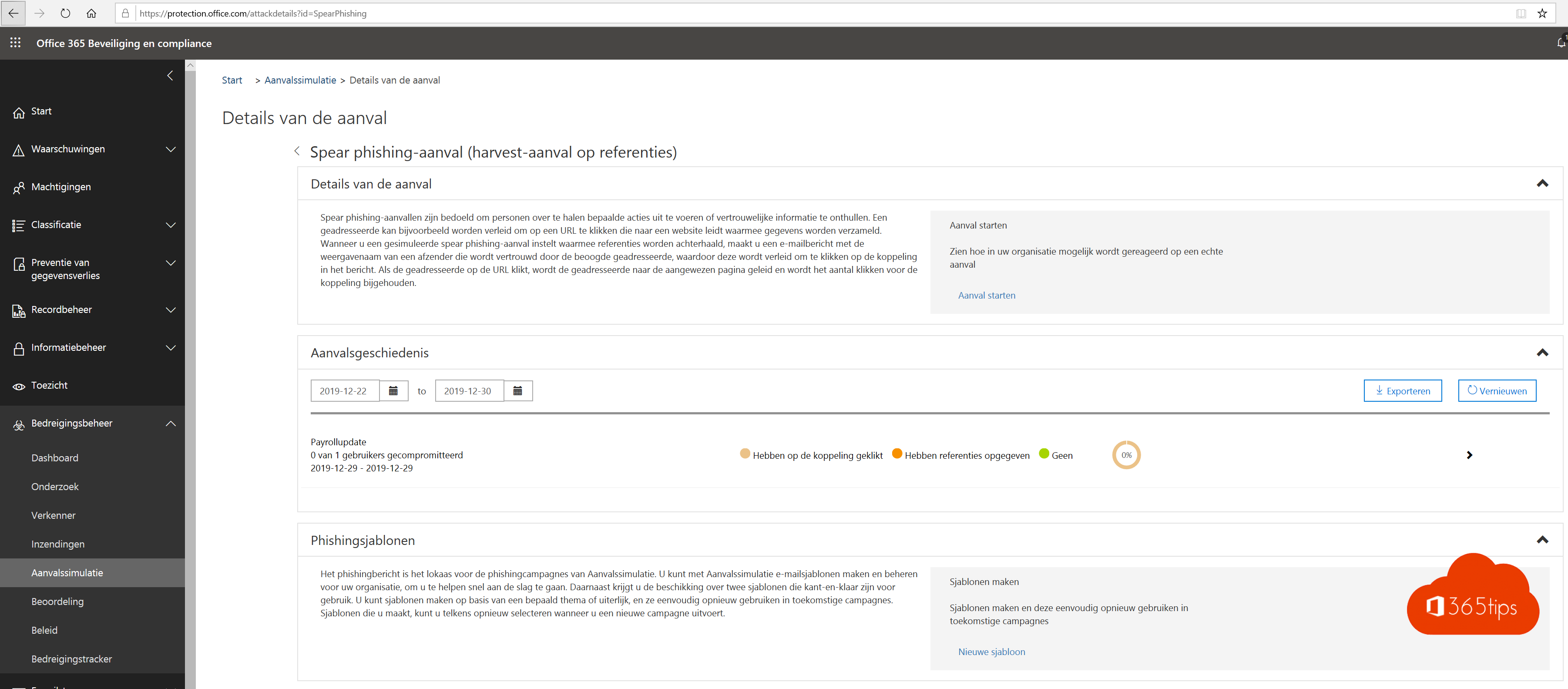
Aanvalssimulator
Activeer een demo-licentie van Microsoft 365 E5 via admin.microsoft.com en activeer deze op je huidige gebruiker.
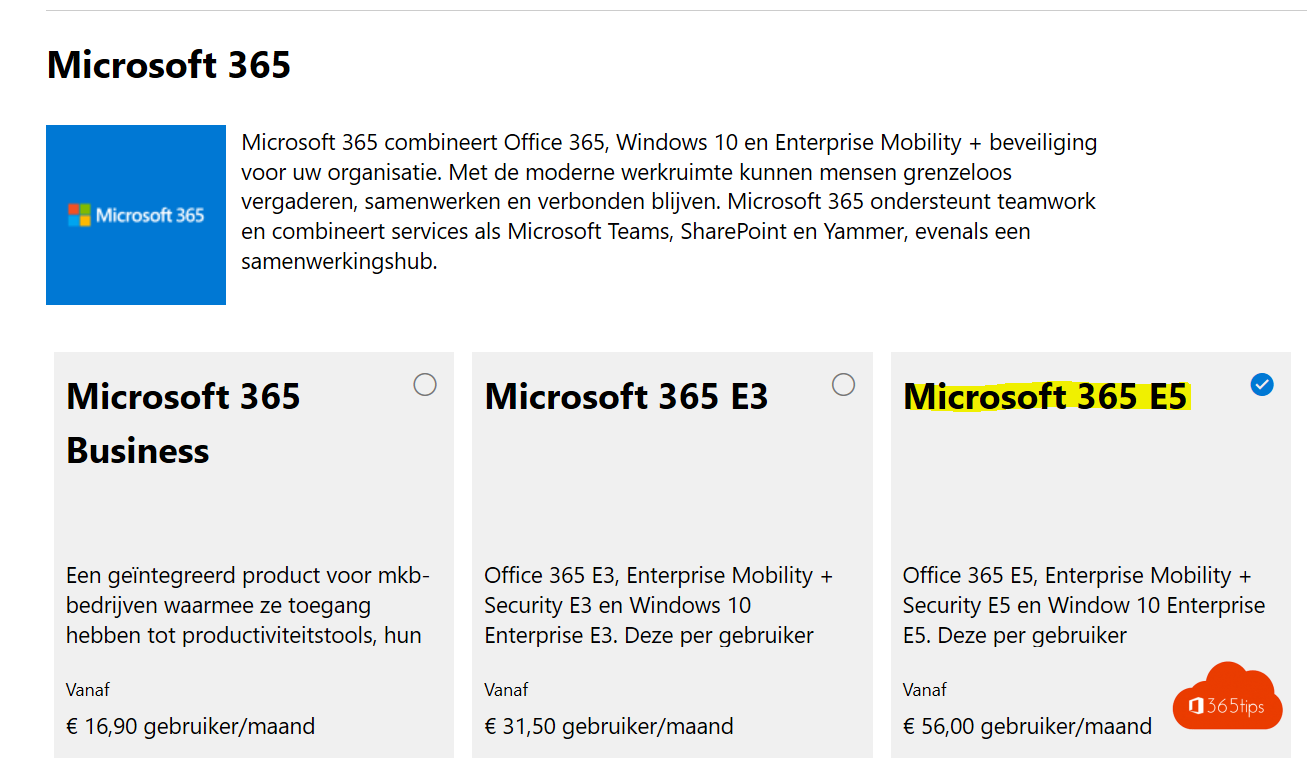
Doe een attack-simulatie waarin je iedereen binnen je organisatie wil vragen om hun loonbrief of persoonlijke gegevens up-to-date te brengen.
Uiteraard wil je meten hoeveel gebruikers hun gebruikersnaam & wachtwoord invullen. Meestal meer dan 30%!
OK. Let’s go! Surf naar de attack-simulator pagina https://protection.office.com/attacksimulator
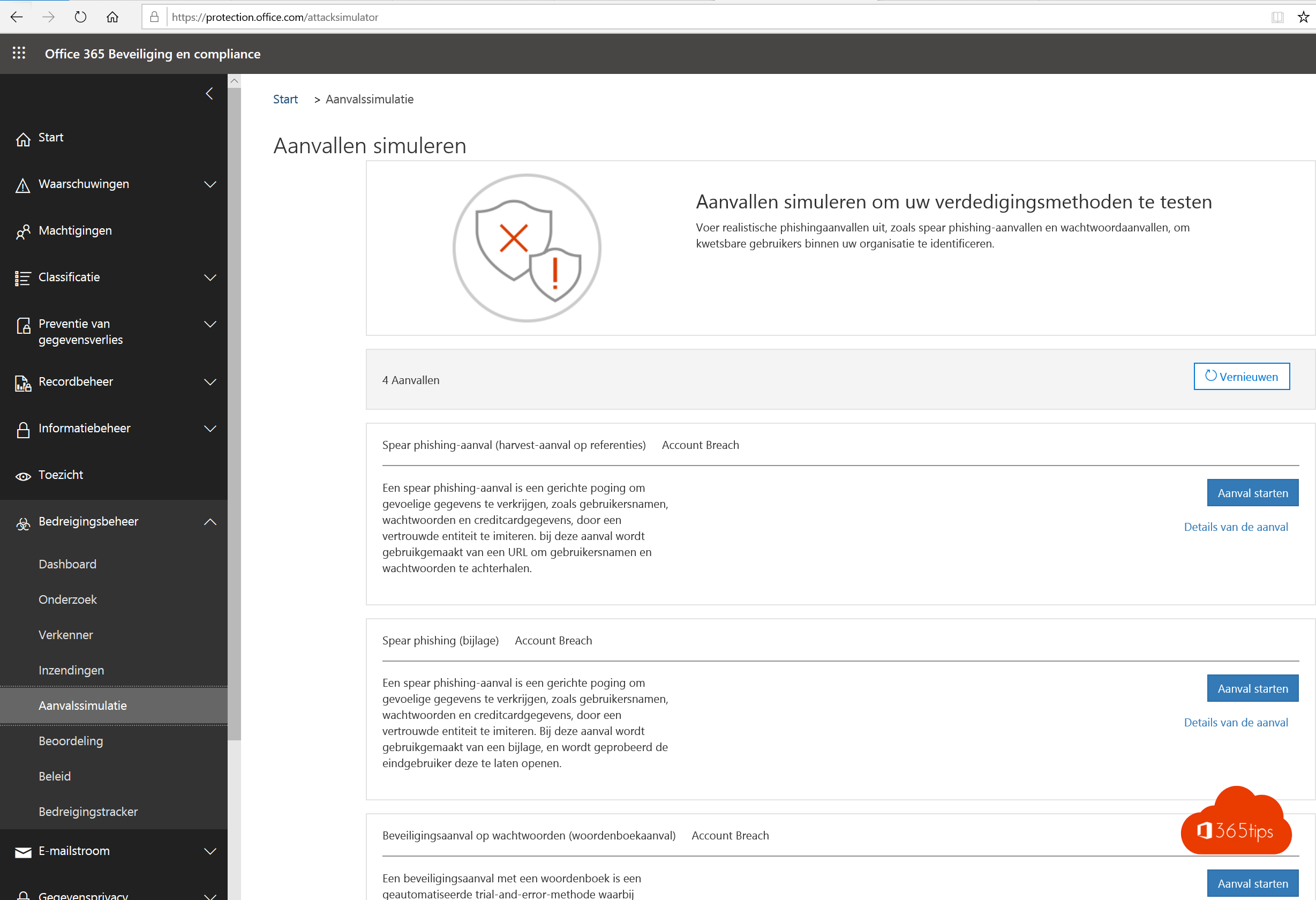
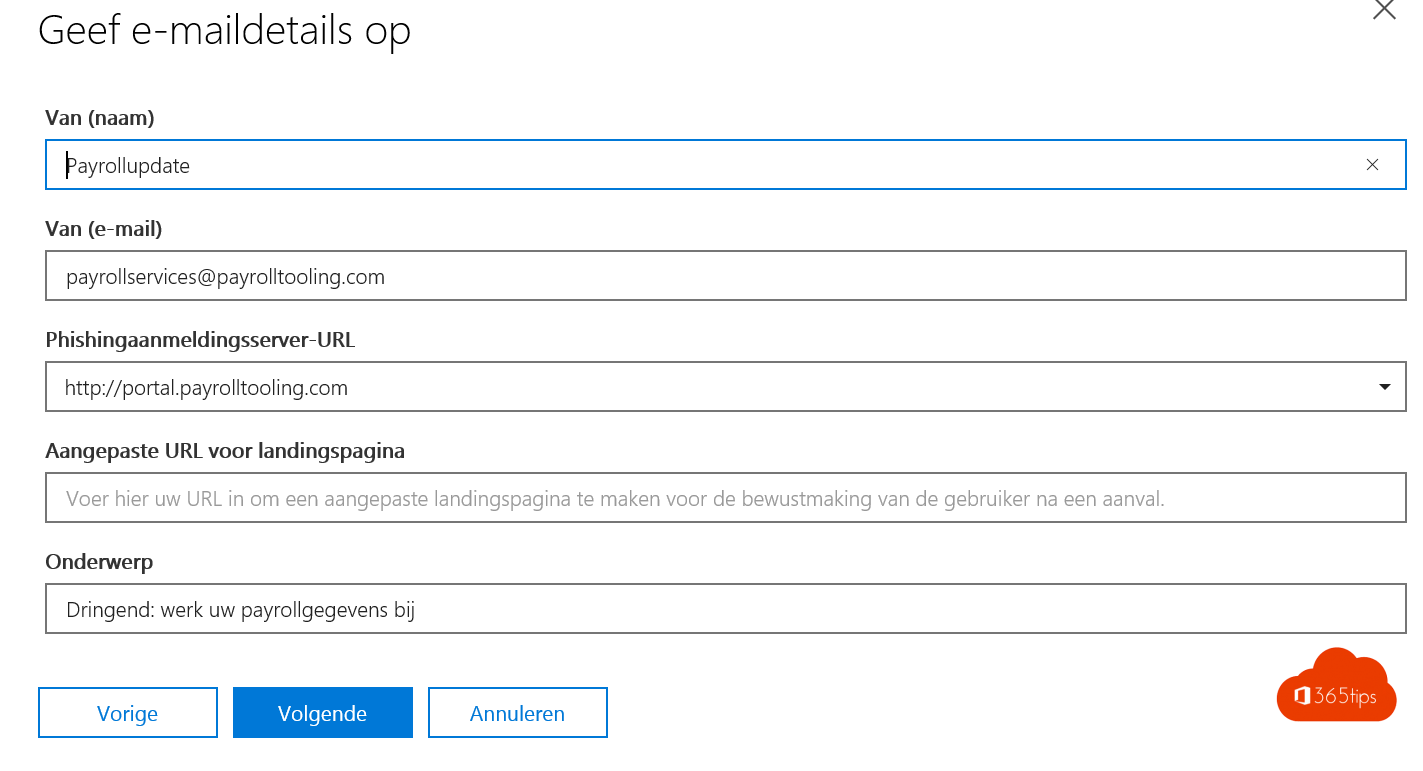
Start een campagne (met bijvoorbeeld een payrollupdate)

Kies personen in je organisatie, best iedereen.
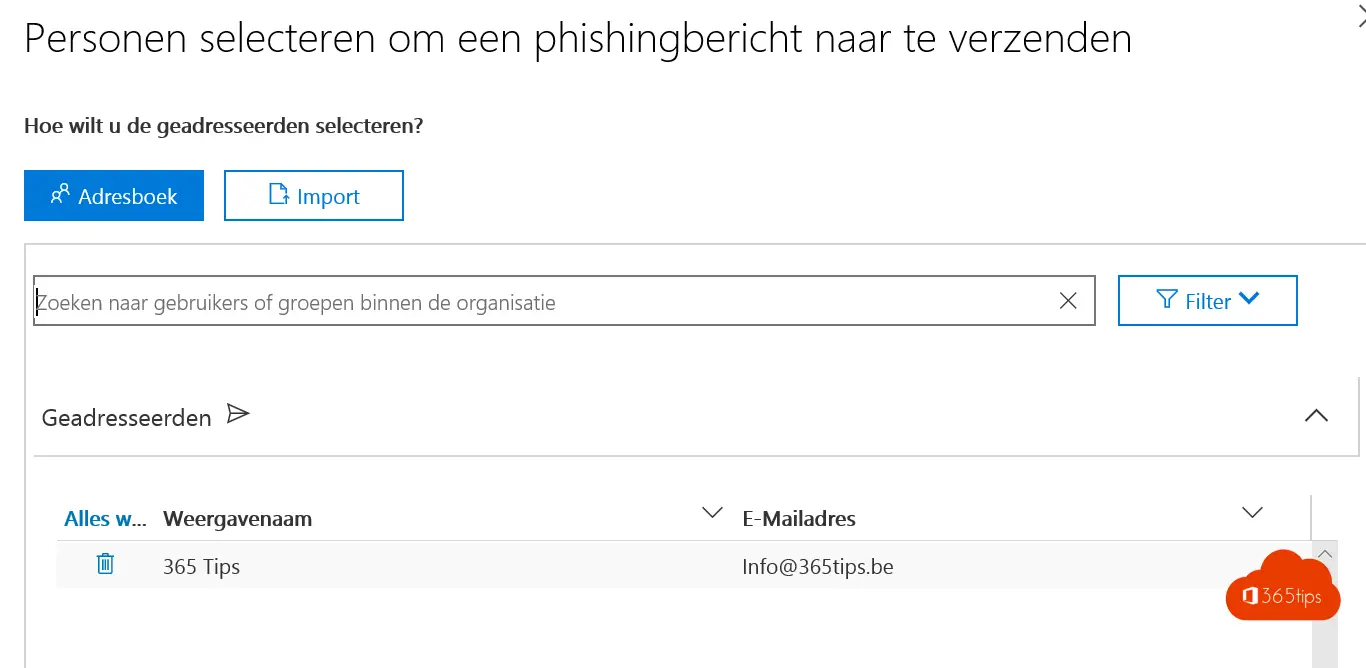
Vul gegevens in die aansluiten met je organisatie.
Gebruik URL’s die lijken op je payroll of loonverwerkings URL’s.
Vul een onderwerp dat aansluit met de actuele updates die je als organisatie gebruikt.
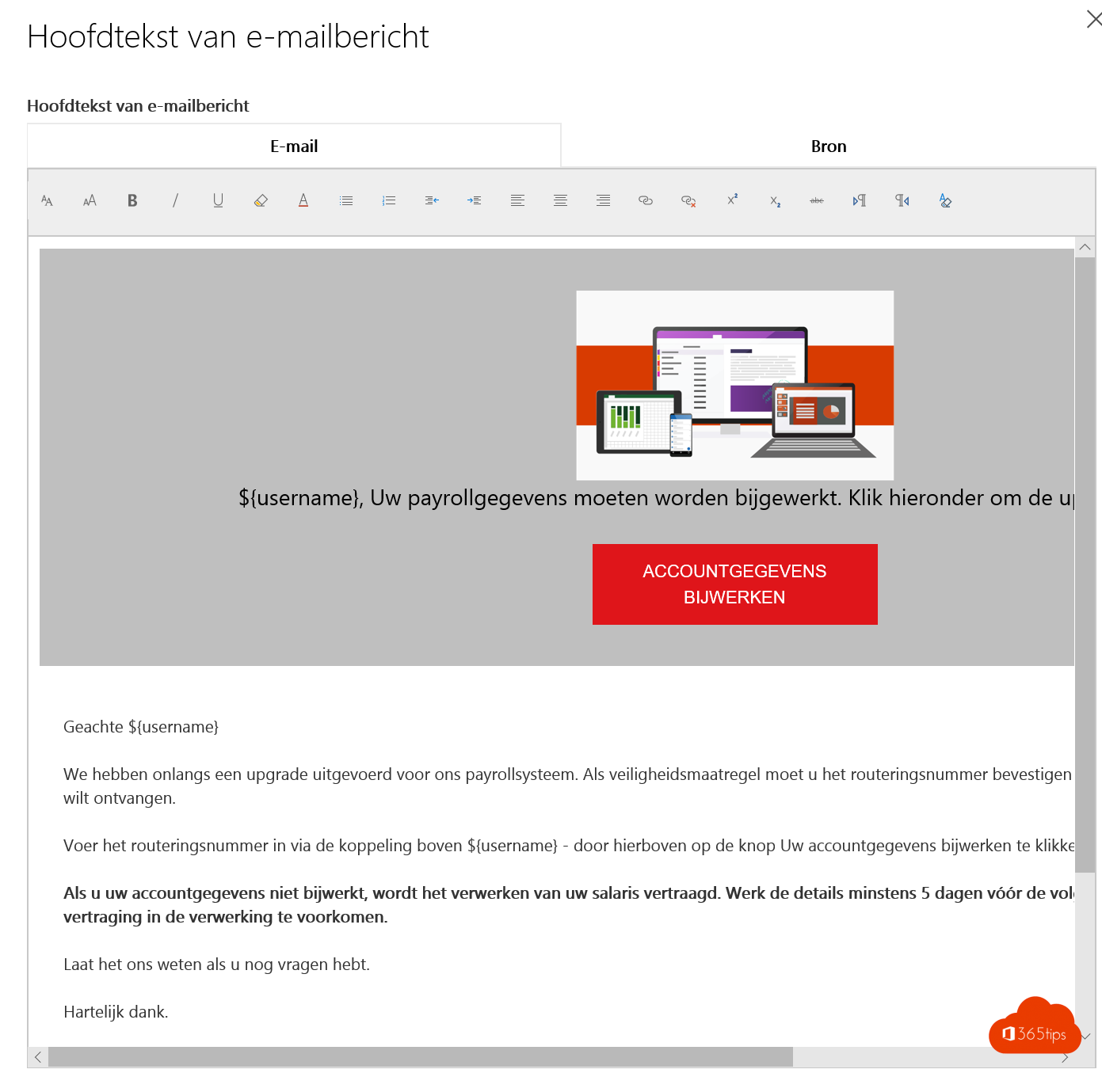
Pas het HTML bestand aan met doel dat deze e-mail er zo goed mogelijk uitziet zodat deze niet afschrikt binnen je organisatie.
Doe de attack via attack-simulator.
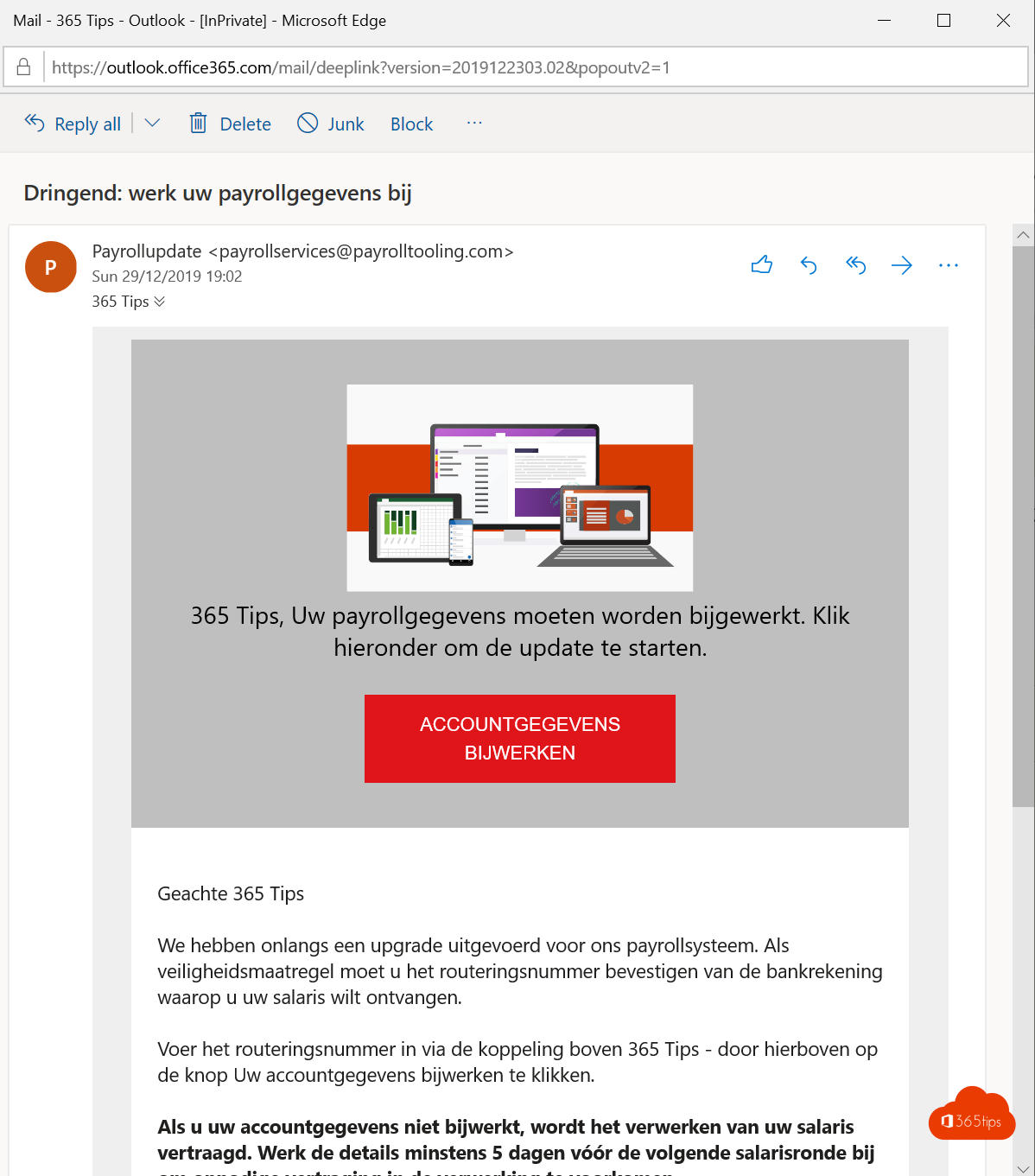
De gebruikers krijgen een email zoals onderstaand.
Ze vullen (hopelijk niet) hun account details in.
Via deze URL kan je de test-attack opvolgen.
Samenvatting
Door meetbaarheid van de attack simulatie kan je cijfers rapporteren om aan te geven hoe belangrijk een MFA implementatie is.
Dit is niet de enige manier waarop credential-breaches of gebruikersnamen en wachtwoorden misbruikt worden. Er zijn ook nog andere mogelijkheden.
Gerelateerde blogs
Miljoenen gebruikers riskeren verhoogde kwetsbaarheid voor aanvallen
Maak legacy authentication inzichtelijk met Azure Log Analytics
Secure Score voor Microsoft Azure
Microsoft Teams security inrichtingen in 4 stappen
de 10 security aanbevelingen die we moeten inrichten nu we thuiswerken!