How to make Microsoft Teams safer for users in 4 steps?
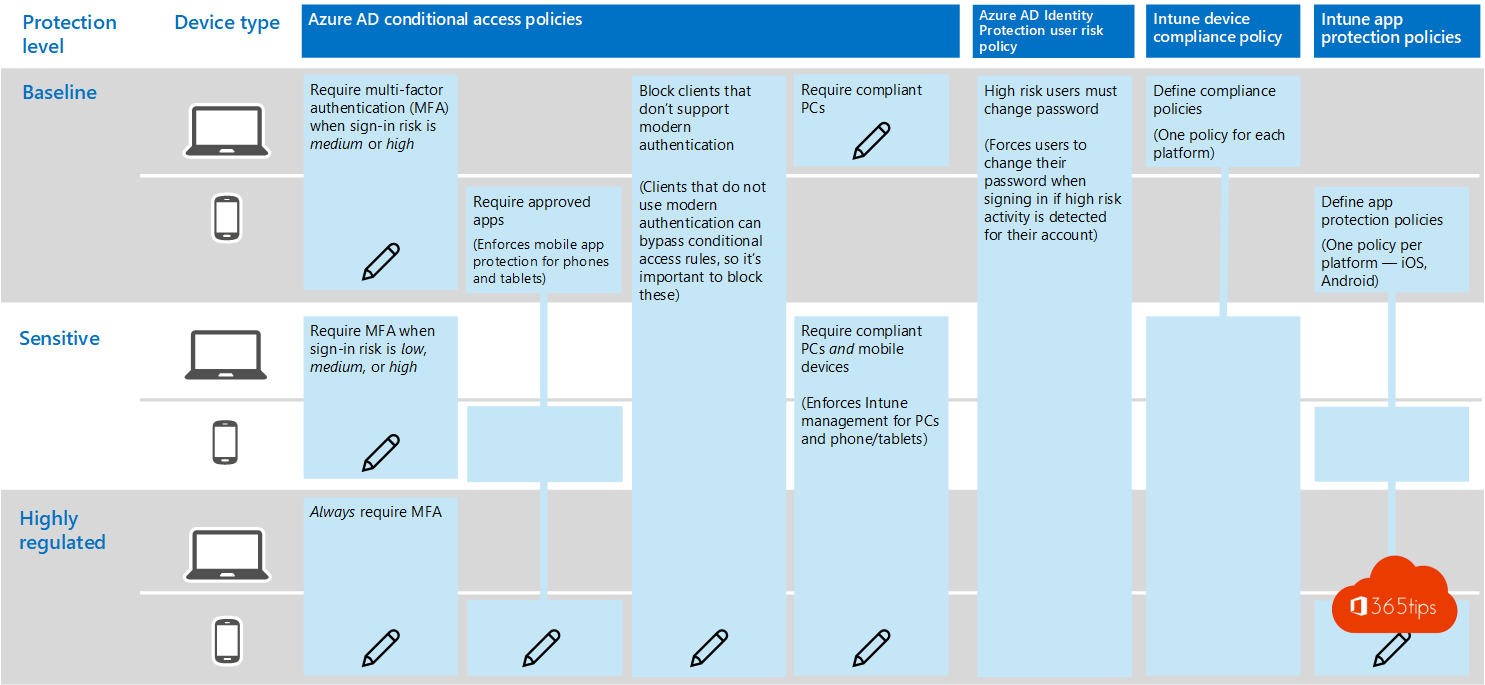
In 4 steps a baseline security setup for every Microsoft Teams rollout? Microsoft tells us what to do - unfortunately few organizations manage to set it up. Too bad, because Teams uses Azure AD. Azure AD uses your on-premises environment and so there you are at the core of your organization. Your Active-Directory environment. We often think that the cloud solution such as Teams are not deeply integrated into the core of your orgasanition. Unfortunately, this is untrue.
To use Microsoft Teams securely, there are 2 key issues to address: identity protection & Data protection.
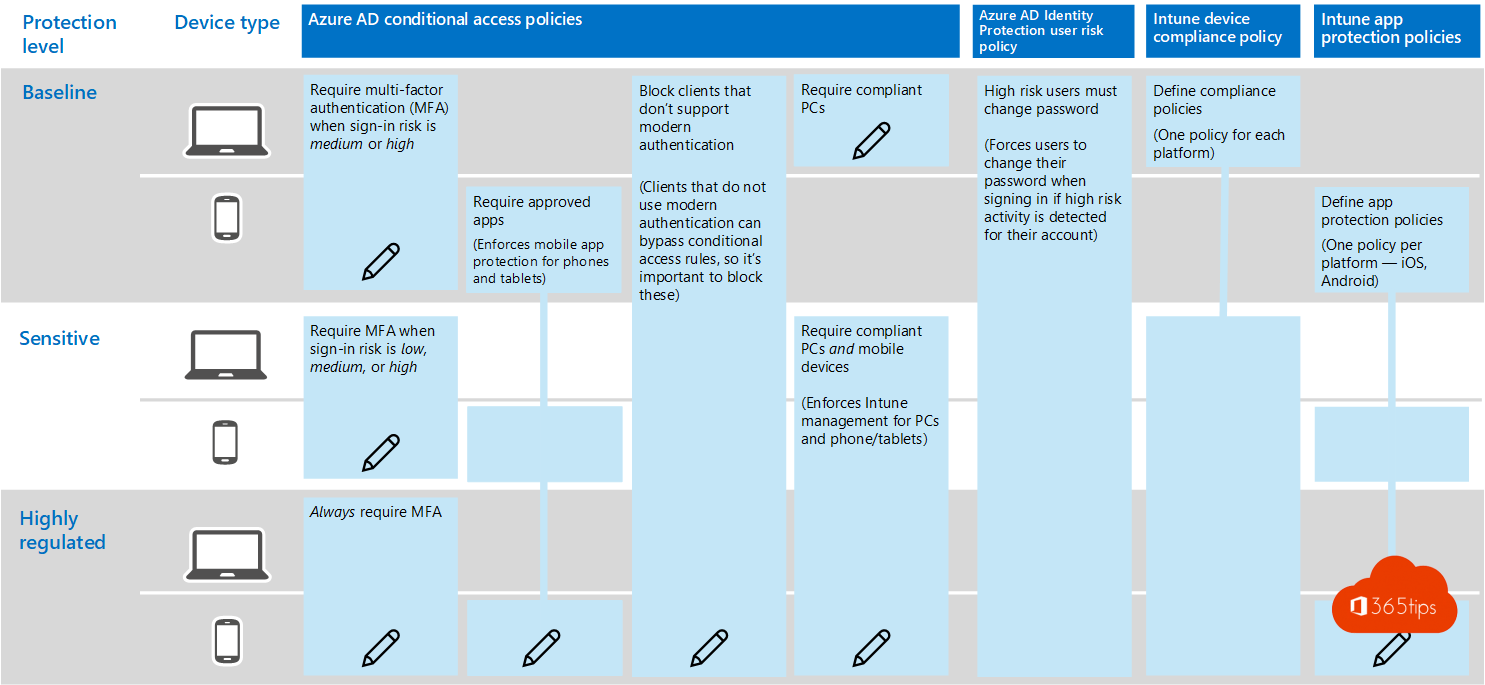
1. MFA + Azure AD Conditional Access Policies.
- As a primary safety enhancement , it is best to activate MFA first.
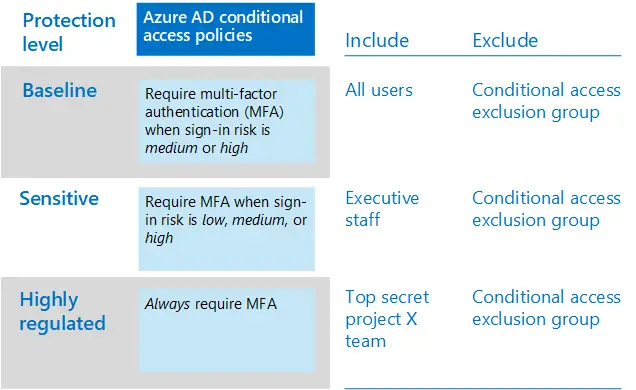
- Before you will activate MFA, it is best to use an MFA registration policy to register users for MFA in advance.
- After users are registered, you can enforce MFA at login.
- MFA is relatively simple. There are also options within Azure AD security defaults. This does this entire process automatically.
2. Azure AD Identity Protection user risk policy.
- To ensure that the compromised accounts of high-risk users are forced to perform a password change at login, it is best to implement a user risk policy.
- If you do not have an MFA, you cannot let users change their passwords. They will be blocked. And a sign-in risk will appear in Azure Active Directory. It's an added value for users to have MFA enabled because they are able to change their password themselves in the event of a risk. Where before they had to contact their IT department.
- A policy must also be created to make this setting active after activation. Useful here is that IT admins can also use these "conditions" on other identity-based Azure AD integrations.
- You can activate this policy in 10 clicks.
- Browse to: IdentityProtectionMenuBlade/UserPolicy
- Create a policy for user risks
- Click on all users
- User risks: Medium or High
- Enforce policies ON

- Remember to turn password change requirements ON.

3. Intune App Protection policies.
- App security policies (APP) define which apps are allowed and what actions they can perform with your organization's data.
- More easily expressed. Organizations often don't know where to start.
- Compliance policies provide a starting point for getting the organization "better under control.
- The APP data protection framework is divided into three different configuration levels, with each level including the previous level:
- (Level 1) Enterprise Basic Data Protection.
- (Level 2) Enterprise enhanced data protection.
- (Level 3) Enterprise high data protection.
- Creating a policy is easy via the Policies menu of Device Cmplaince.
- Browse to: Https://endpoint.microsoft.com or via this direct link: DevicesComplianceMenu/policies and activate a compliance policy.
4. Intune Device Compliance policy
- Device compliance policies define the requirements that devices must meet to be marked as compliance.
- If you want to create your own policy you can get started via: intune device compliance policy from the Microsoft Endpoint Manager management center. https://endpoint.microsoft.com
- Create a policy for each platform:
- Android
- Android Enterprise
- iOS/iPadOS
- Macos
- Windows Phone 8.1
- Windows 8.1 and above
- Windows 10 and above
More information can be found about these policies at Microsoft Docs: https://docs.microsoft.com/nl-nl/microsoft-365/enterprise/identity-access-policies#define-device-compliance-policies
