These are the top 10 security recommendations when working from home using Microsoft 365
- Identity Security / MFA.
- Install the latest patches and updates to software and systems
- Change usernames and passwords regularly
- Build real-time reports of security risks
- Create automated and intelligent alerts
- Install antivirus software or all endpoints
- Secure private devices and business devices (+ phones)
- Regularly evaluate which users have access to data, devices and networks
- Track, change and block access for temporary projects and when employees leave the company
- Use information protection (information management) solutions to protect your data everywhere, no matter how it is processed.
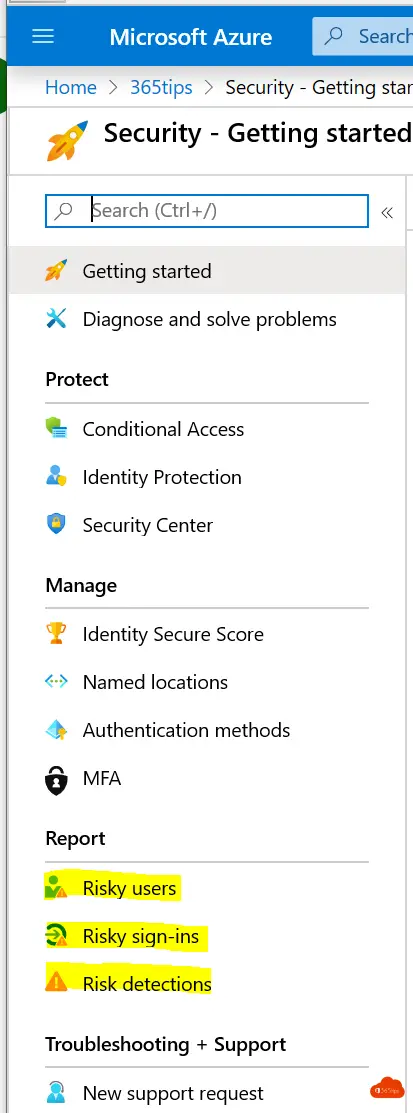
1. Identity Protection
1.2 million Office 365 accounts (per month) are hacked. This represents only 0.5% of all accounts on your environment. Source: theregister-co-uk
In figures:
| 0.5% of accounts on: | 100 |
| That's 1 account up: | 200 |
| 2 accounts on: | 400 |
| 4 accounts on: | 800 |
Multi-factor authentication prevents 99.9% of all attacks
- Activating Mfa is easy and can be done based on this article.
- Want to know how many people today press their passwords in non-secure websites. Do this atttack simulator.
- Risky accounts can be accessed via: risky sign-ins.
- MFA & MAP, POP3, block in one click with automatic activation and roadmap. -> Azure-ad-security -standards

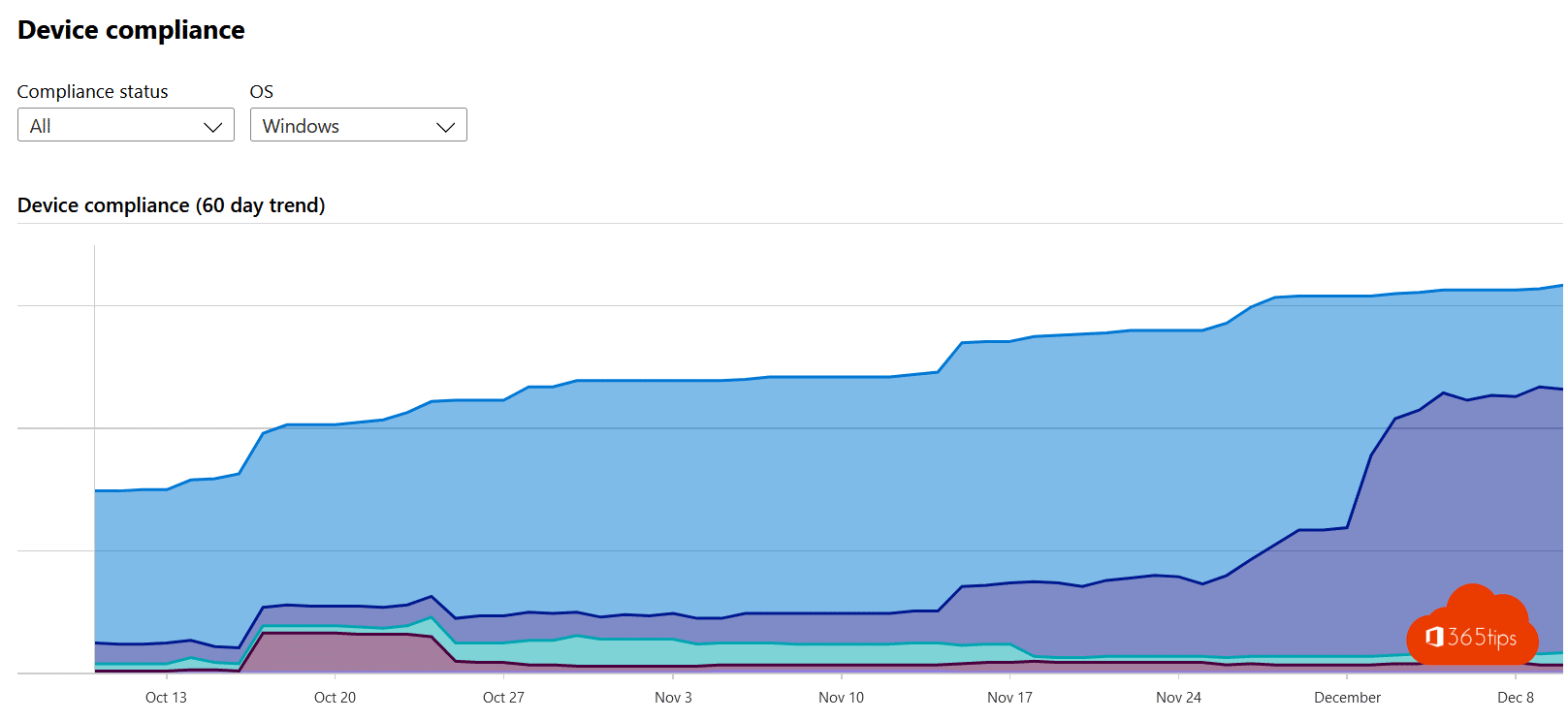
2. Patching & updates.
- Make sure you have all computers and servers under control.
- Use a tool that manages to keep an inventory of all computers.
- Intune can help; other solutions exist.
3. Change passwords regularly
- If it is not so easy to change passwords it is best to work with MFA. This removes the password problem for many cases. Documents and applications today are often in the cloud. MFA can protect Office 365 & M365 well.
- In the latest security baseline, Microsoft recommended to stop changing passwords. This combined with MFA is a good solution.
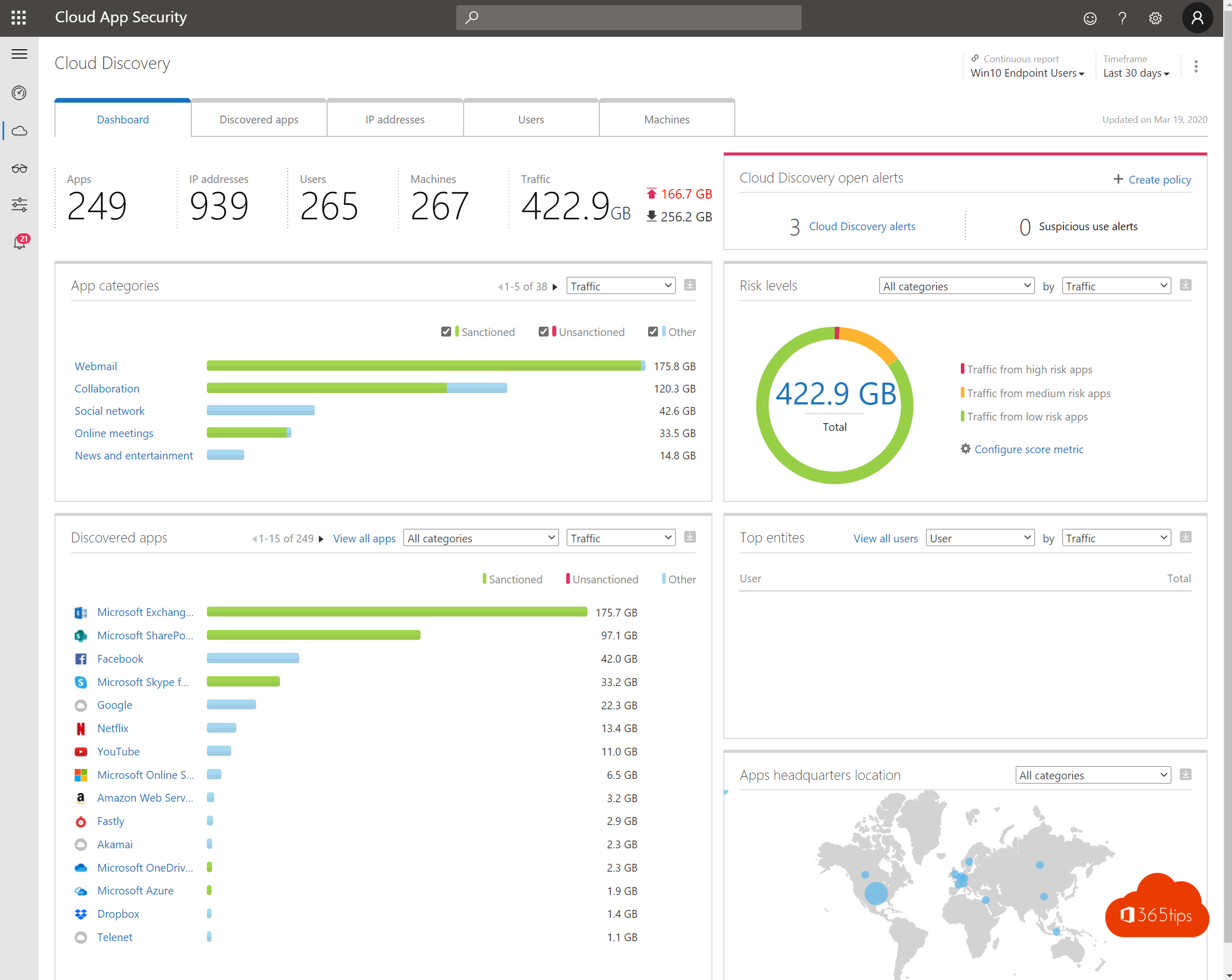
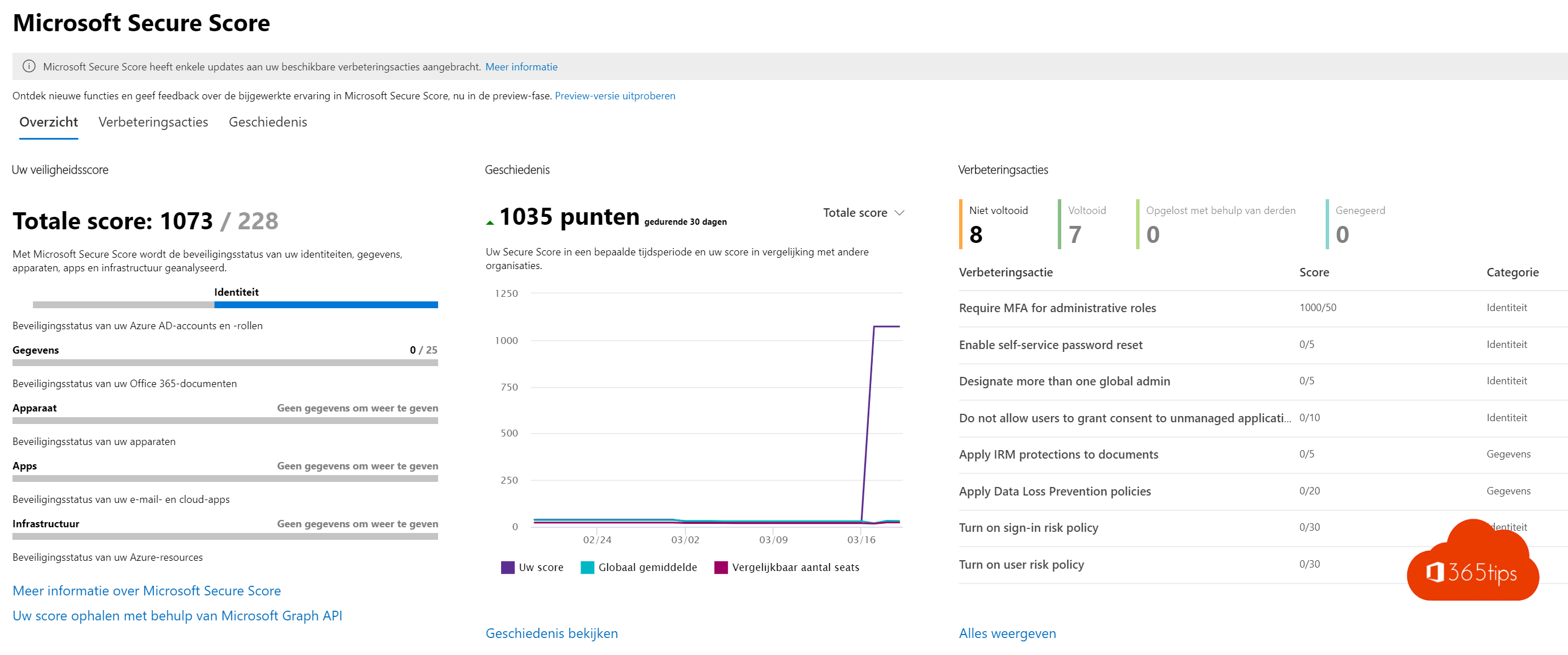
4. Build real-time reports of security risks
- Identity risks are common and remain one of the greatest risks.
- Easy to understand these is a security assessment you can do yourself at 2.
- There are also device risks such as malware etc. these can be looked into with Microsoft Defender ATP.
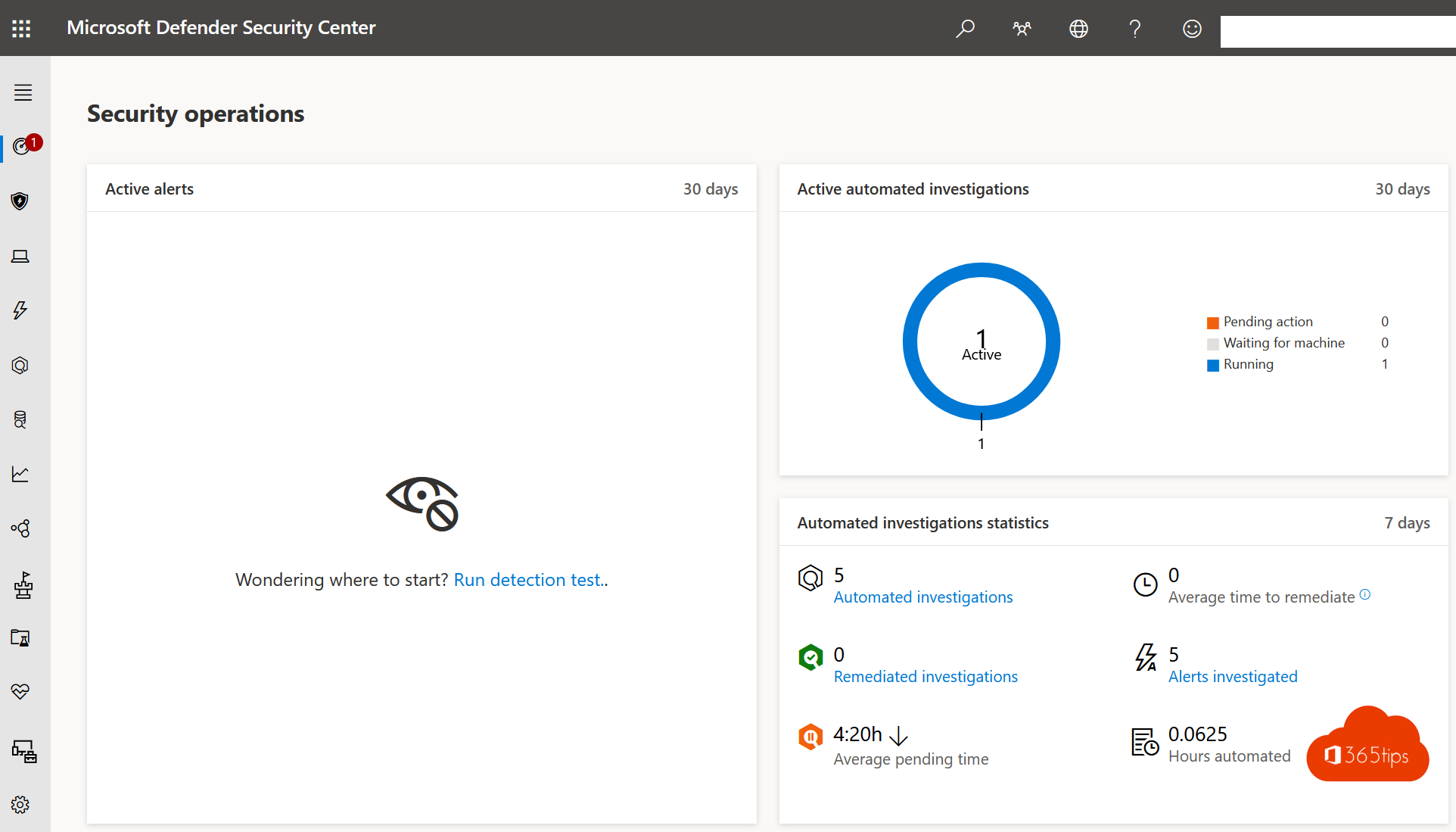
5. Create automated and intelligent alerts
- Cloud App Security gives the ability to automatically act upon a risk. For example, you can set an alert if someone distributes 20 documents.
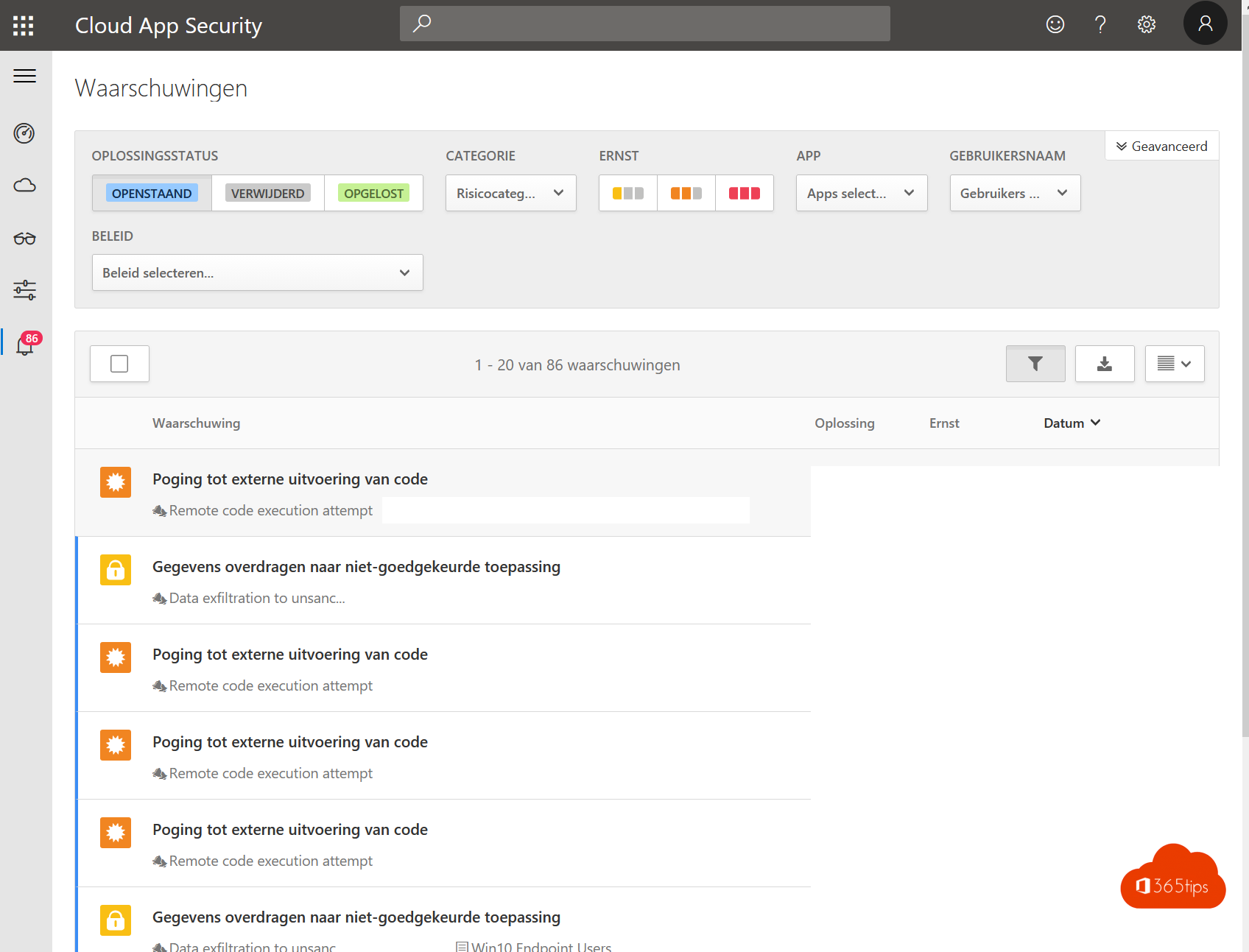
6. Install antivirus software or all endpoints
- MDATP, sentinelOne, Norton, Mcafee, it doesn't matter per se. As long as you manage to provide antivirus at each endpoint. MDATP allows for easier integration.
- Another aspect is being sure your antivirus is enabled. It's best to do that from this console.
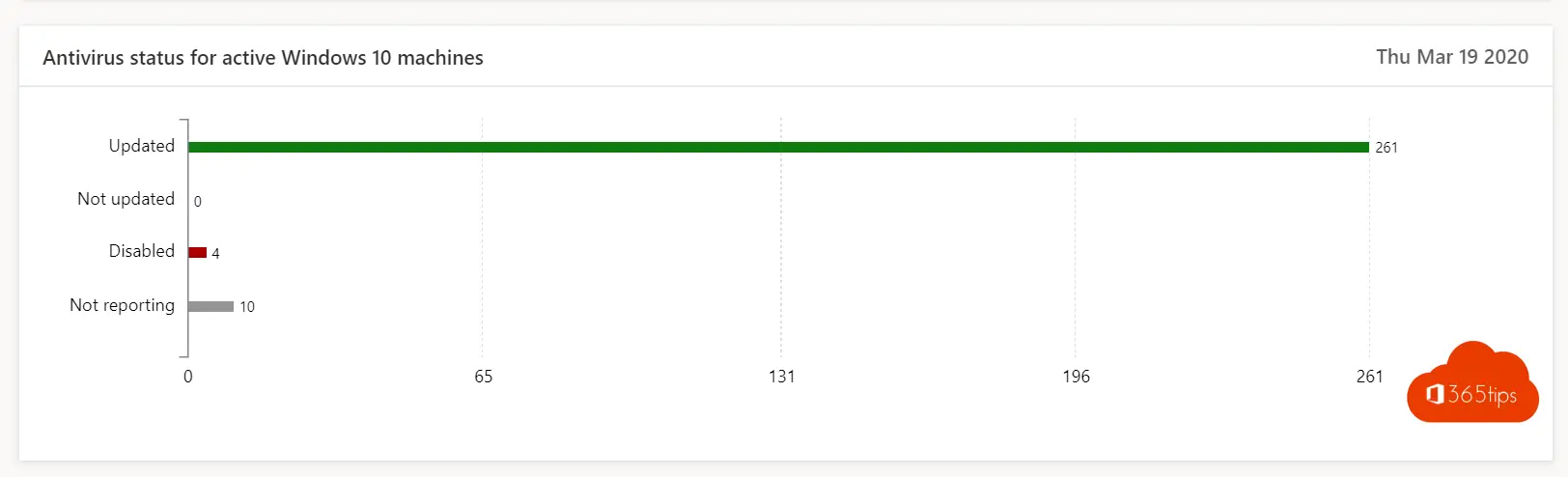
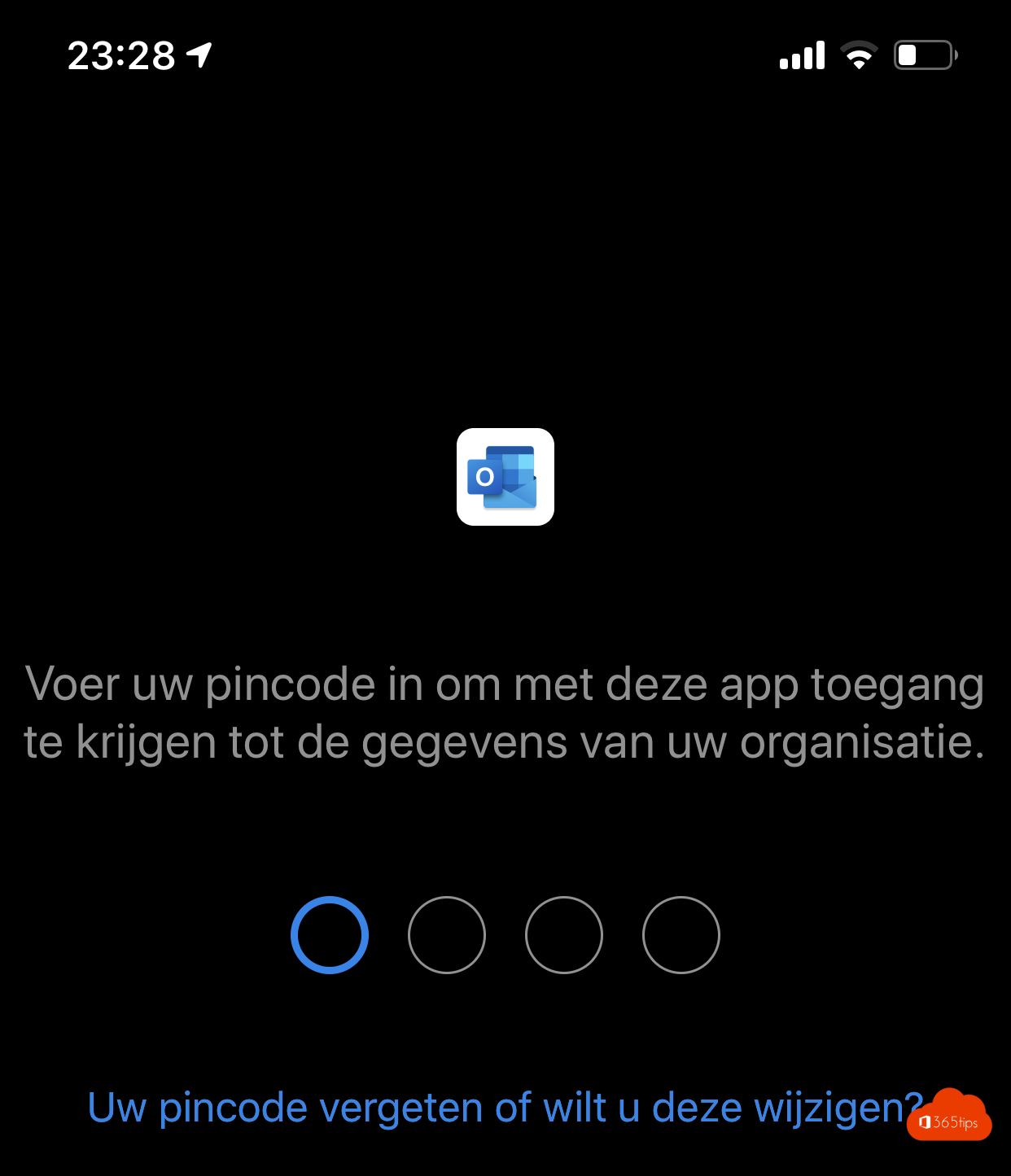
7. Secure private devices and business devices (+ cell phones)
- We often manage to properly protect our fixed PCs, laptops. Mobile devices often don't. Through Intune, you can isolate and segment applications without having to manage the device. The application is in management. The organization's data is protected.
- On the one hand with a PIN, fingerprint, faceID. On the other hand, you cannot copy documents to other applications so the data remains secure.
- This is an example of the Outlook App. shielded on a BYOD.
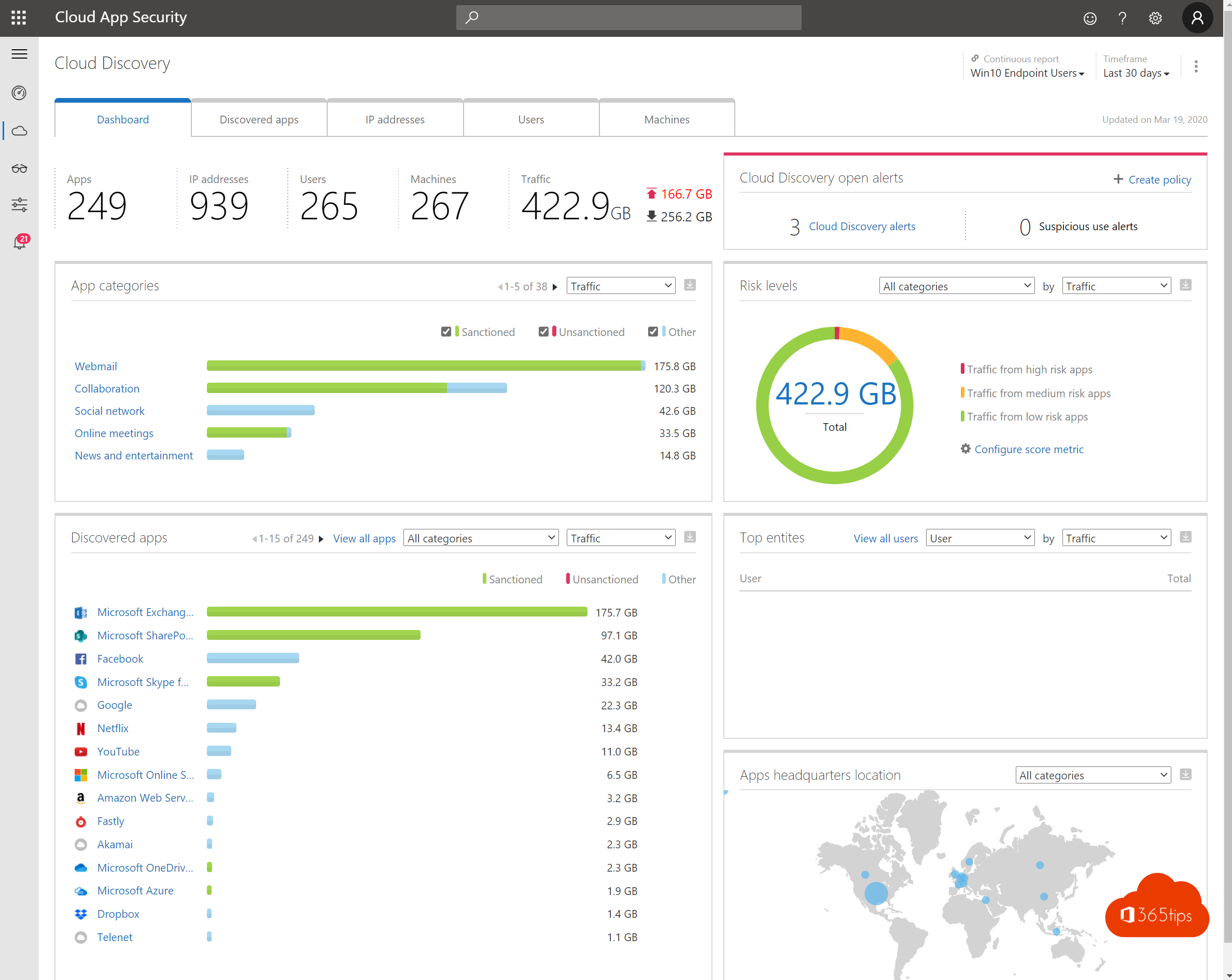
8) Regularly evaluate which users have access to data, devices and networks
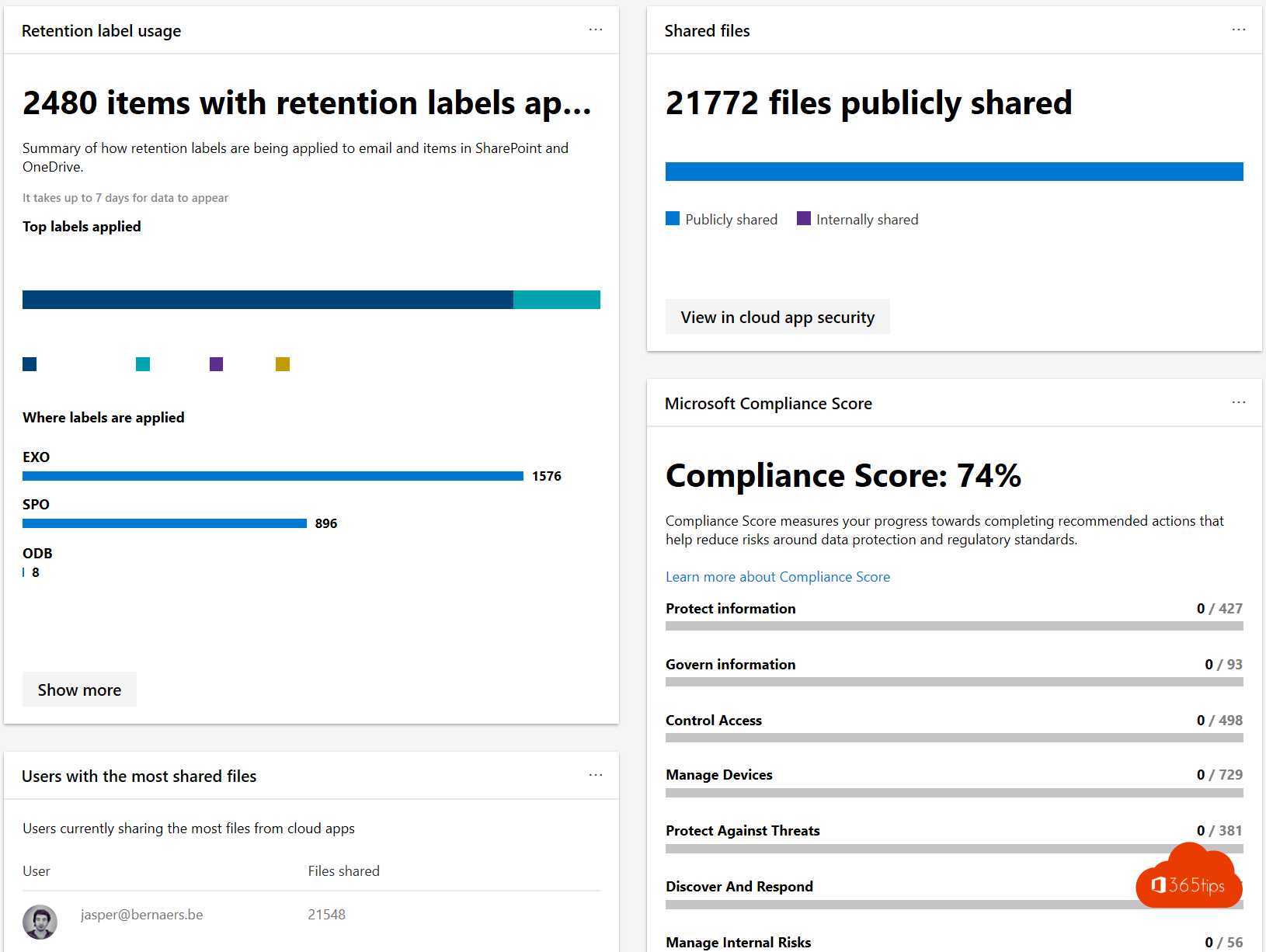
- Cloud App Security shows you how data lands on endpoints.
- You can pullreports from current information security to identify the movement of data flows. Document data, but also identity properties. (place, location)
9. Track, change and block access for temporary projects and when employees leave the company
- governance without enforcement is just good advice.
- Create rules and arrange it technically.
- A microsoft Teams site for a project exists for 6 months. after that you can automatically delete it.
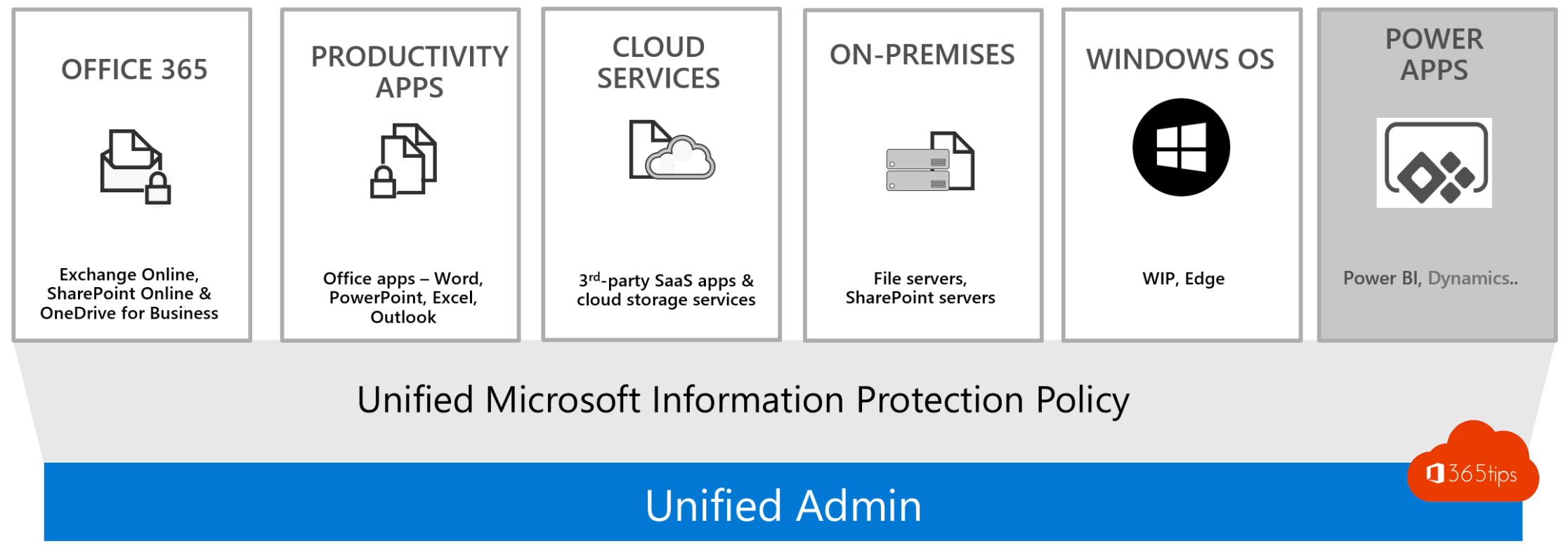
10. Use information protection solutions to protect your data everywhere.
- Information protection provides berscherming of the document. Even if you were to "physically" lose the document. There is still the possibility of blocking it.
- Are you able to pull a report from current shared documents?
Conclusions
Setting security priorities is not easy. I would always start with MFA and identity security. Then document and device security.
If your identity is not secure, there is no point in doing information protection. Because a "hacker" will log into your account and be able to access your documents.
Also read
Installing Windows 11 with Microsoft's installation assistant
How to listen to Spotify through any web browser
These are the 10 success factors when setting up Microsoft Teams
Subscribe
Login
0 Comments
