🔐 How to activate Multi-Factor Authentication in Microsoft 365 (MFA)
1. Why Multi-Factor Authentication?
Microsoft wrote in advance in their security blog. You have 99.9 percent less chance that an untrusted person can access your Office 365 account if you don't have an MFA.
A 2nd factor is really necessary. Often hackers already have your password in their possession.
So activating MFA to protect your identity is important. If someone gains access to your mailbox, that person can also abuse your identity. It is appropriate to protect not only your mailbox but also your Google Account, your Facebook, PayPal and other accounts you use.
2. What is Multi-factor Authentication?
Multi Factor Authentication (MFA) is a way in which authentication is granted using an additional factor. Or multiple factors.
Something someone KNOWS such as a password or a pin code
Something someone HAS such as a cell phone, a 'fido2' hardware token
Something someone IS like their Biometric data: fingerprint or facial recognition.
3. How to enable Multi-factor authentication as a user - The latest way
Here you can set up your MFA and adjust settings yourself as an end user. At the bottom of the page, as an IT Administrator, you can roll out the entire organization with MFA.
Browse to: https://aka.ms/mfasetup and open the Microsoft Multi-Factor Authentication page.
Login with your current account.
Click next
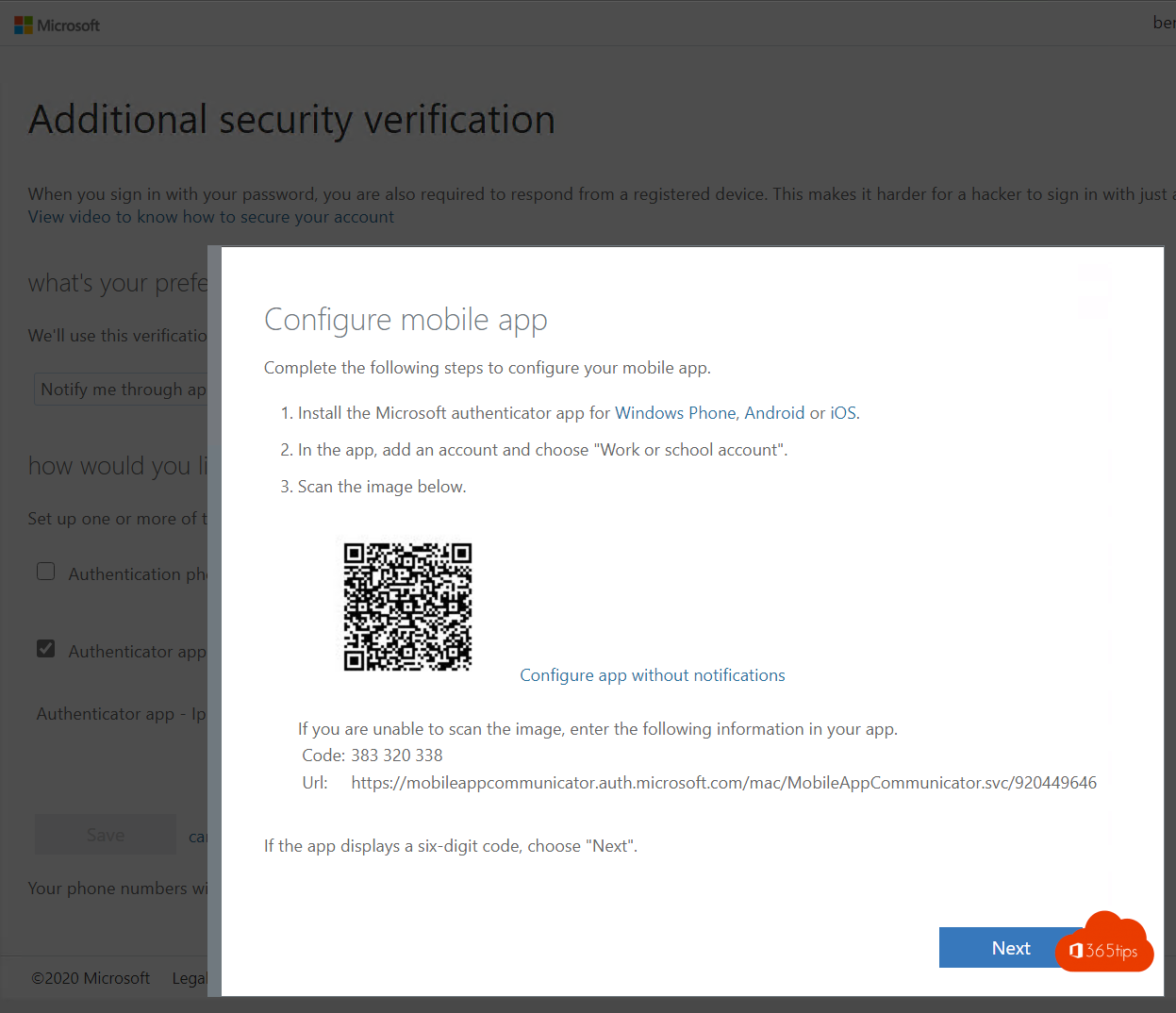
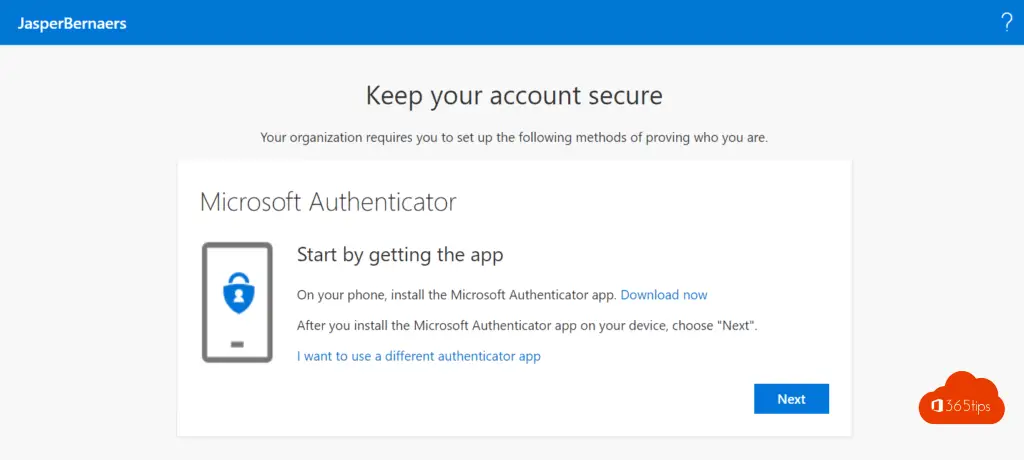
Install the Microsoft Authenticator app on your iPhone or Android phone.
Press next
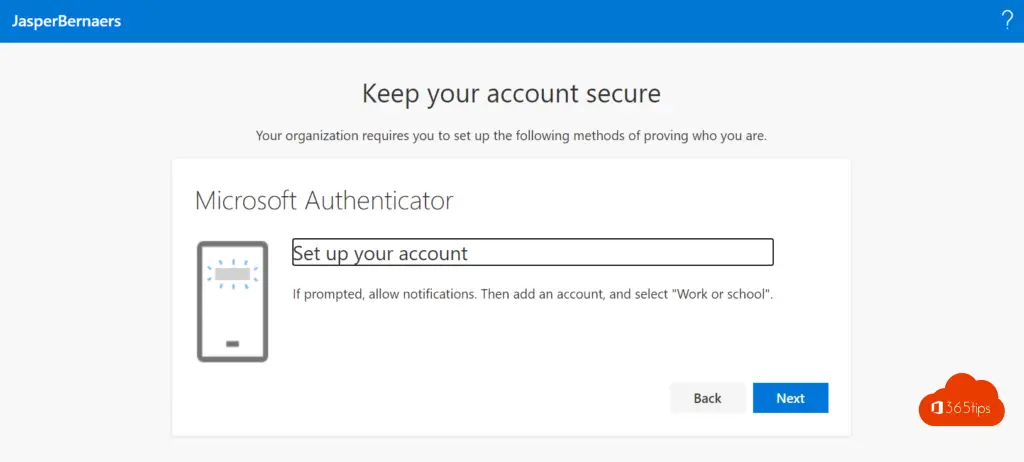
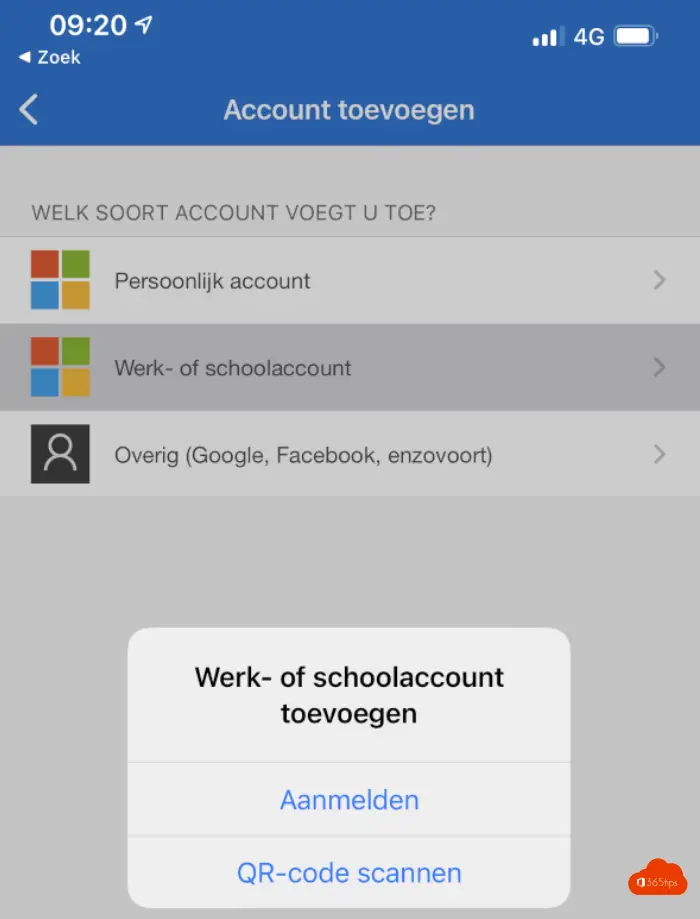
In the mobile application, choose add work or school account.
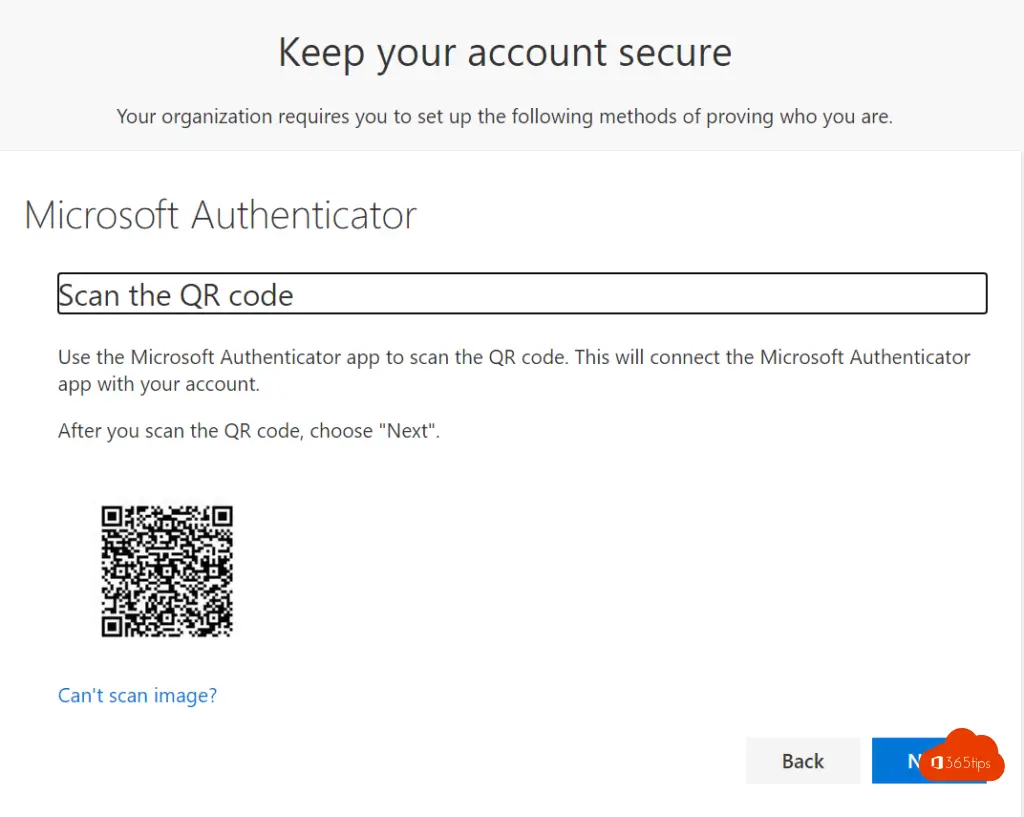
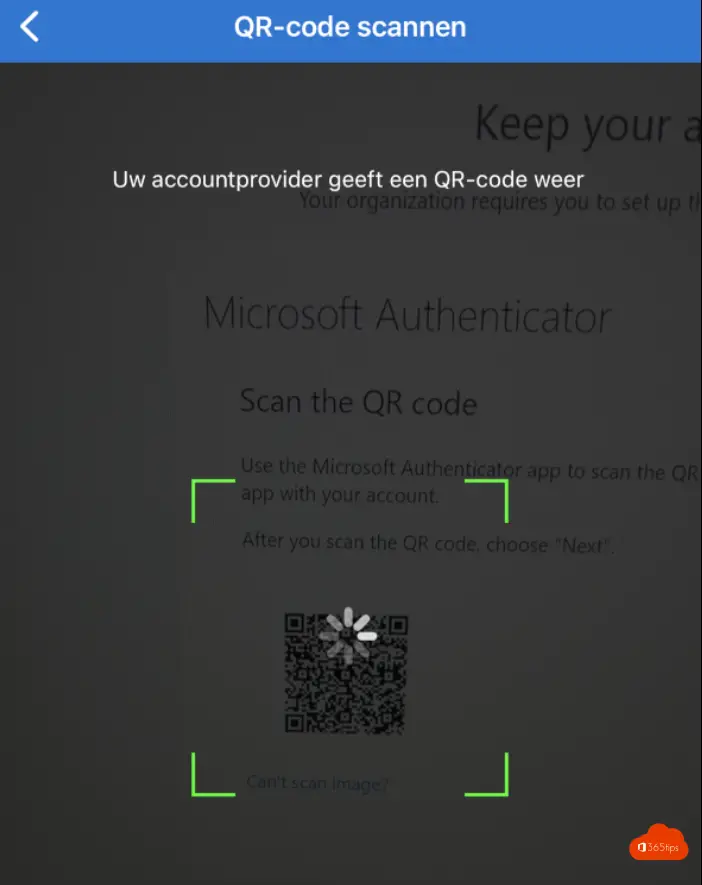
Scan the QR code
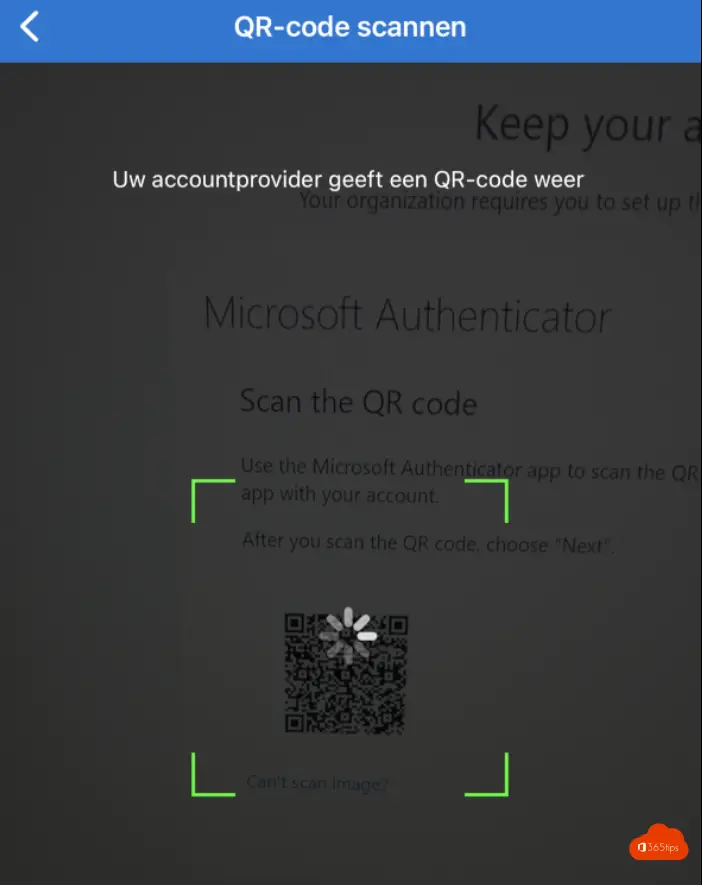
Scan the QR Code via the Authenticator App - mobile
And now a brief test from Microsoft.
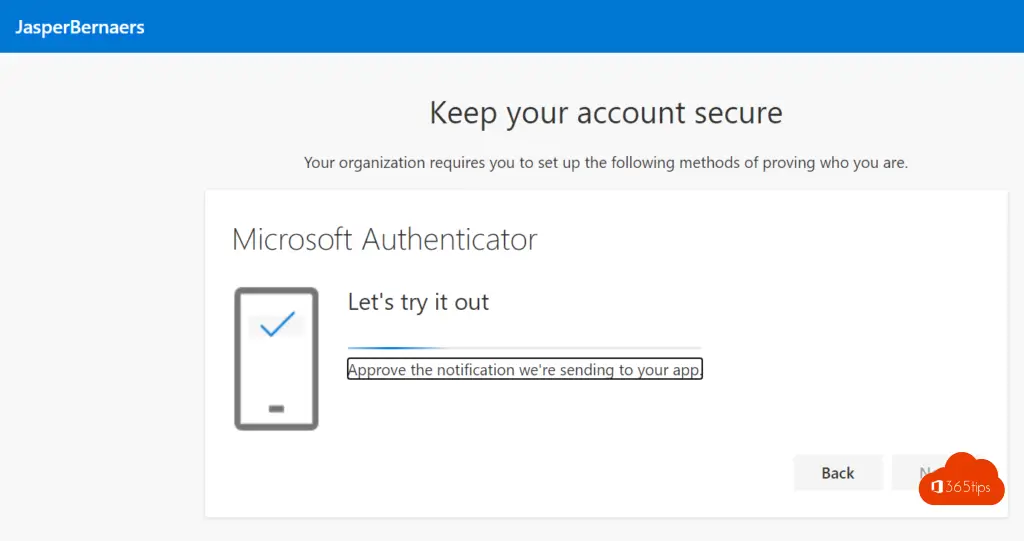
Activation has succeeded! Test in an inprivate browser to make sure everything is correct after activation to make sure nothing went wrong.
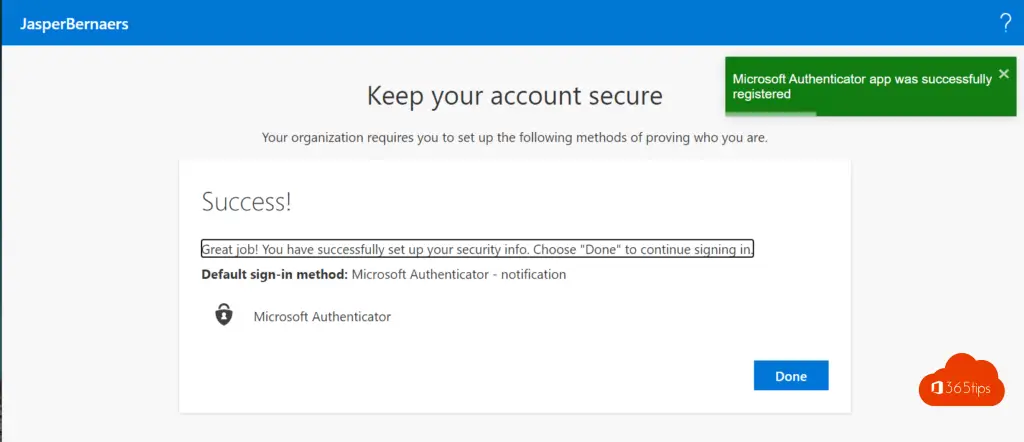
4. Enable MFA for users - Or reset current settings
Browse to: https://aka.ms/mfasetup and open the Microsoft Multi-Factor Authentication page.
Login with your current account.

Click next
Choose authenticator app or token - Setup Authenticator App
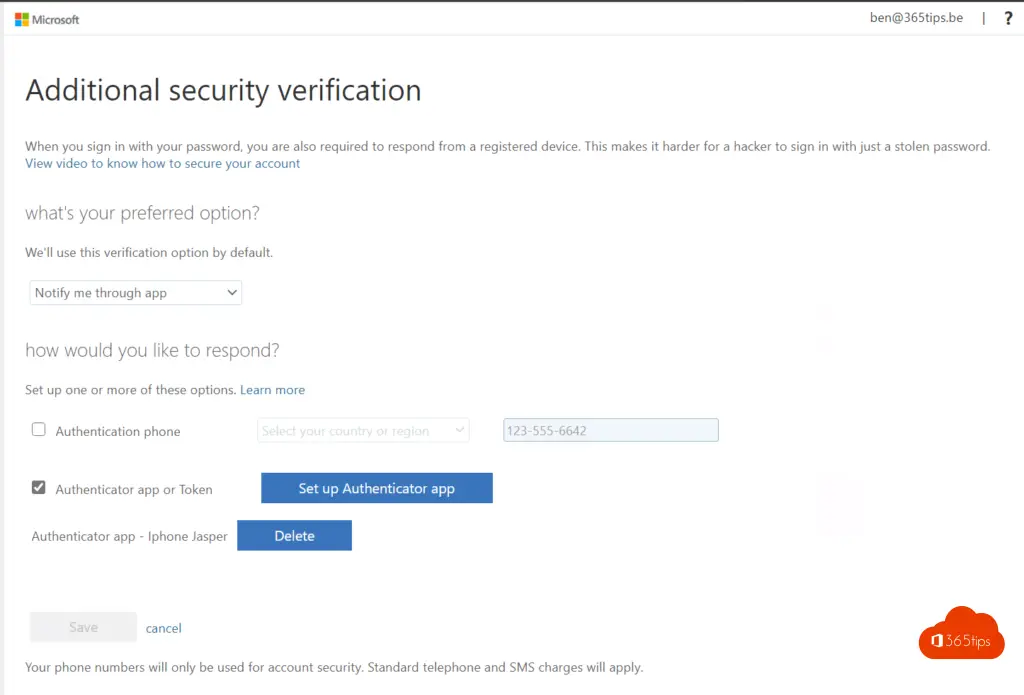
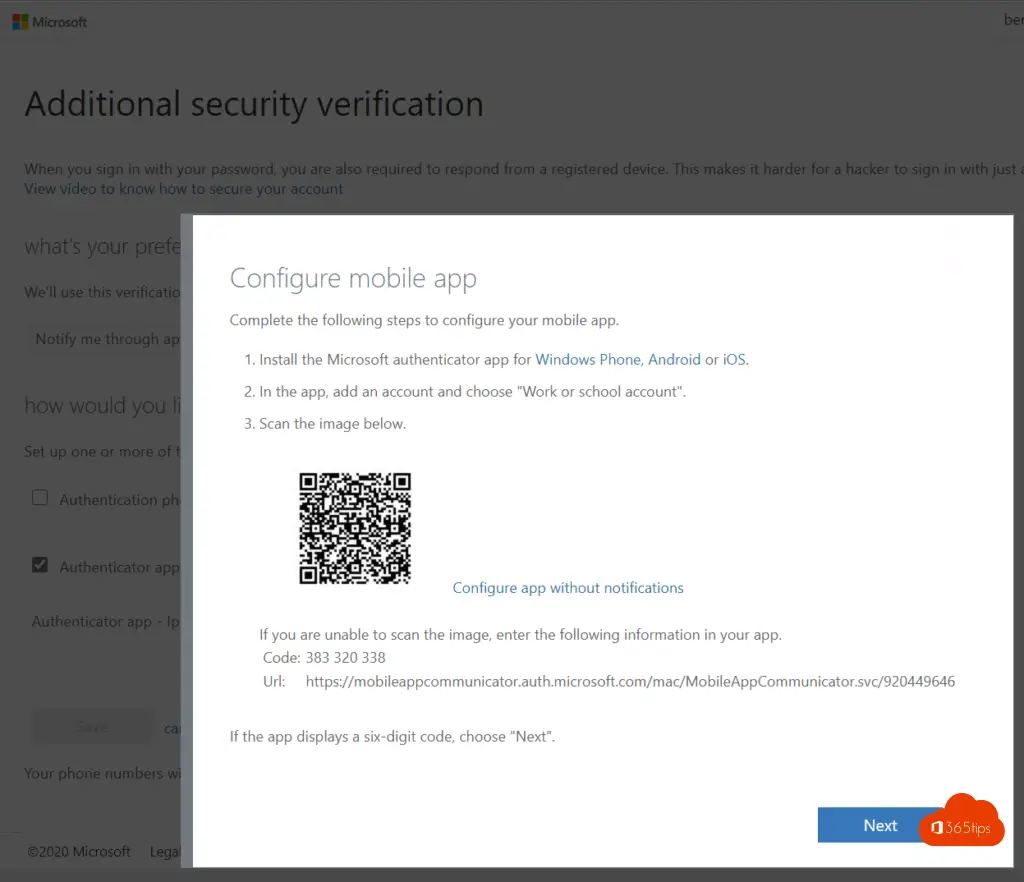
Install the Microsoft Authenticator app on your iPhone or Android phone.
In your mobile app, press the plus at the top to add a work account
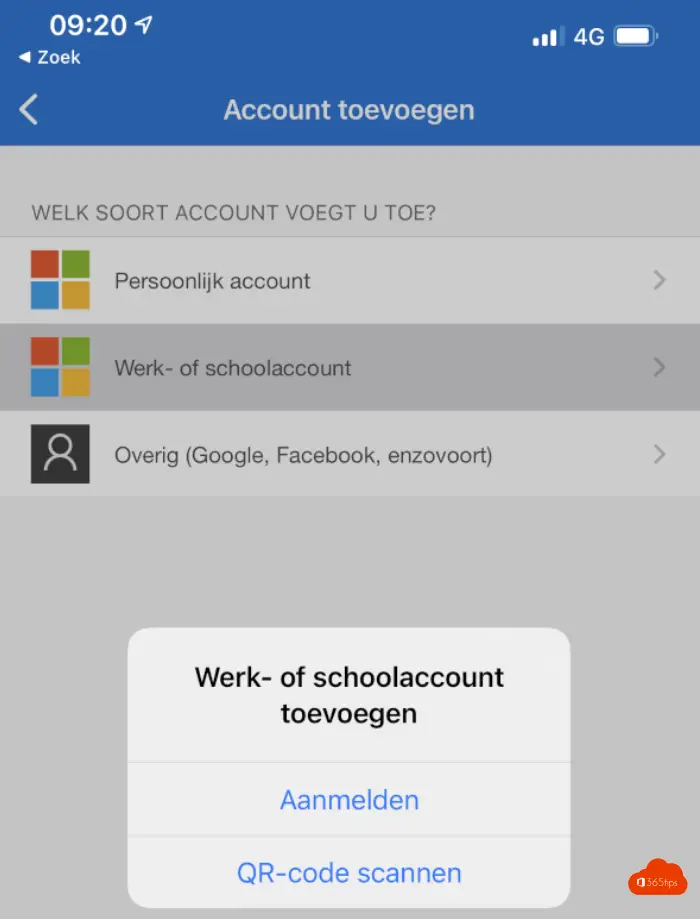
Scan the QR code obtained by pressing Set Up Authenticator App
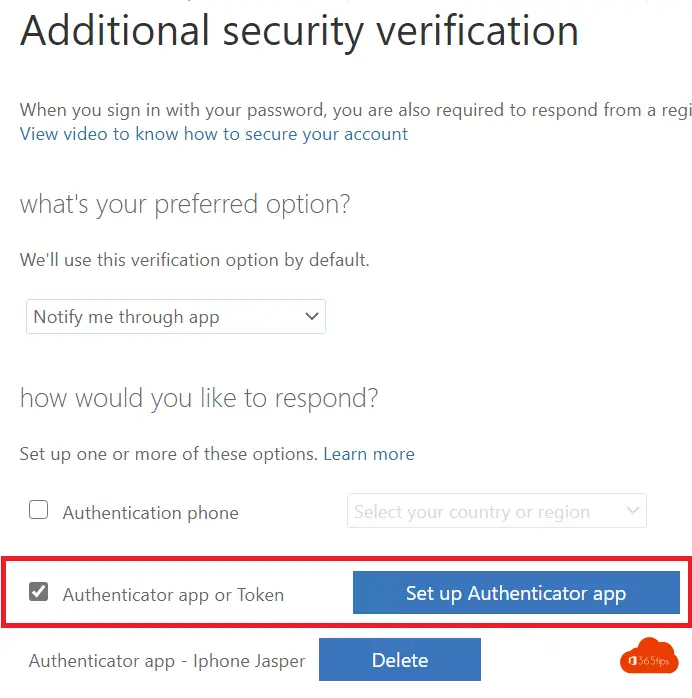
The code appears in the web browser.
Then scan the code
Click next.
You get a prompt on your phone click Accept.
As of now, your mobile device is known as a 2nd factor. This doesn't necessarily mean that your IT Administrator has set policies so that this is a standard from now on. But you are already ready to use MFA.
Using the Authenticator App as your primary login method
At https://aka.ms/mfaset up, you can choose to provide the alerts via the authenticator app or via text message.
It is recommended to use the app because it is very user-friendly and gives more features on your smartphone - and more security!
You can make this adjustment in the screen below. After you have logged in to https://aka.ms/mfasetup
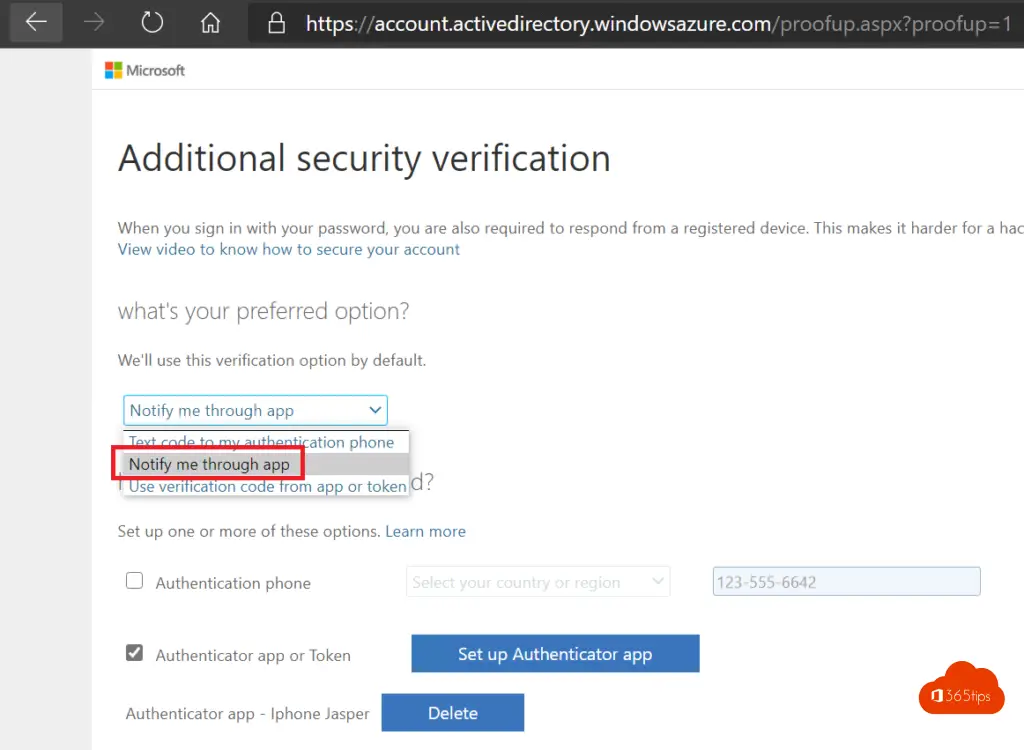
Lots of MFA fun!
The guide above allows users within your organization to activate MFA themselves. Unfortunately, that is not enough. If you want to get it right, and you are an IT Administrator, you can work with Azure AD Security Defaults.
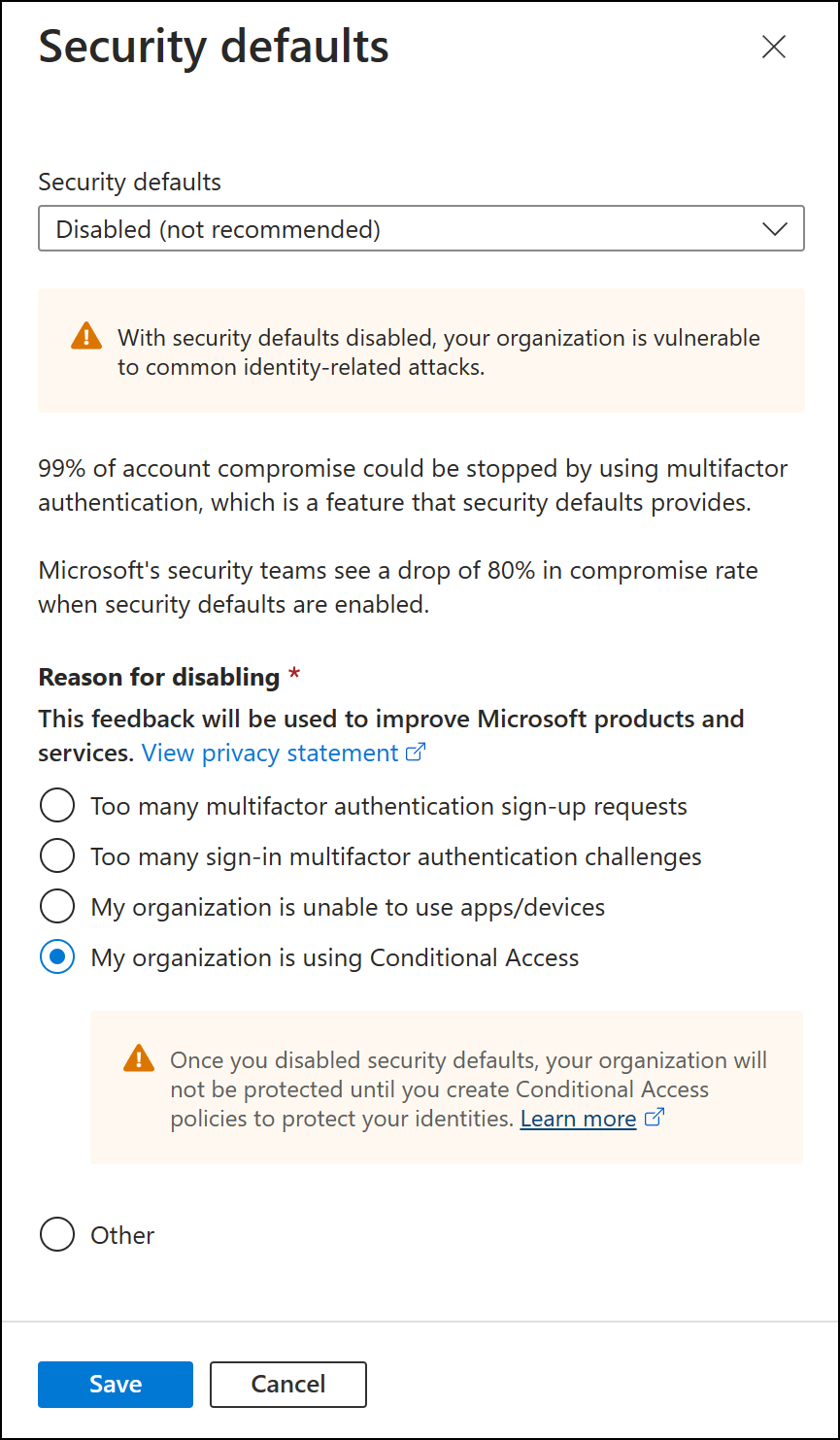
5. Enabling multi-factor authentication for your entire organization can be done in one click with Azure AD Security Defaults
See article.
6. How can you enable Azure MFA number matching?
If you wish to enable Azure MFA number matching, you can follow these steps.
Navigate to Azure Active Directory. In the Security Tab, press - Authentication methods.
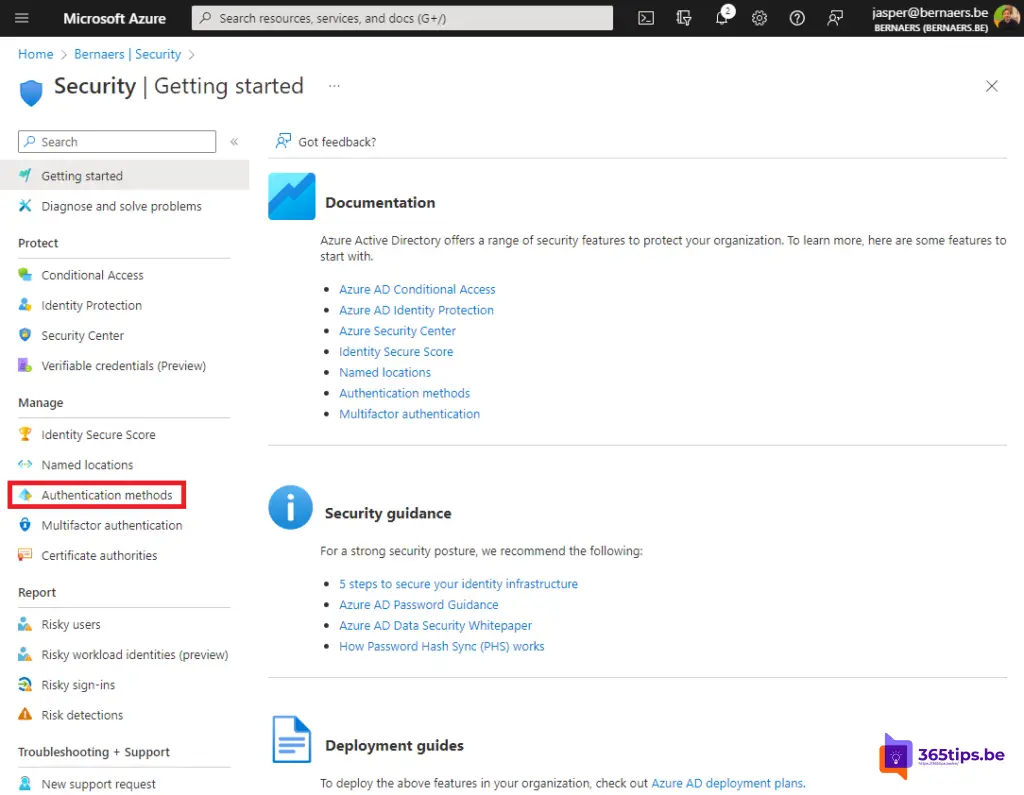
Check that in Microsoft Authenticator settings, the basic settings are correct.
These should be at Basics: Activated.
Target: All users.
Authentication method: Anyone.
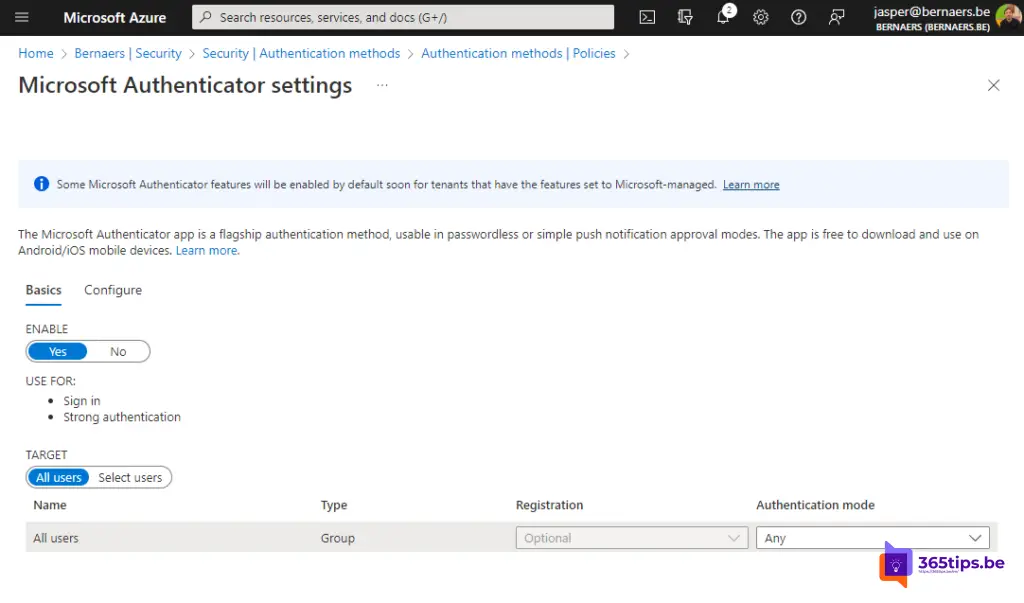
Then press Configure. (Next to Basic Settings)
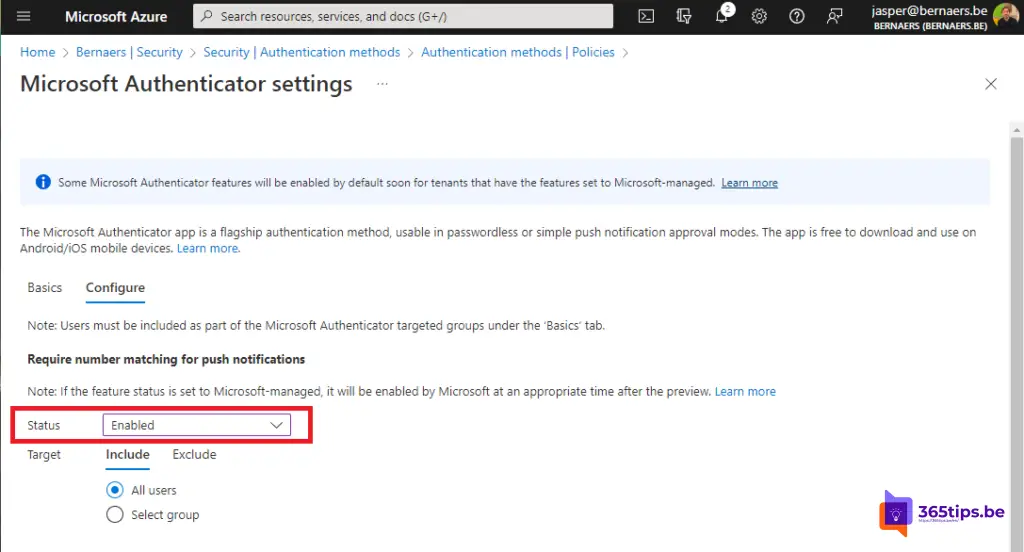
Under: Require number matching for push notifications: Enable.

[...] DocsConfigure authentication session management - Azure Active Directory | Microsoft DocsHow to activate Multi-Factor Authentication (MFA) in Microsoft Office 365? (365tips.be) (Dutch [...]