Starting with Office 365 Secure Score
Given the evolution to Office 365 and Micrsoft Teams , it has become more important to incorporate security systems such as Multi-factor Authentication.
What is the best way to get started? What are the first technical steps of activation?
In this blog, I describe some steps you can take to work more securely with Office 365, Teams and Microsoft Azure.
Awareness campaigns of Office 365
Attack simulator
There are several ways to make an impact within your organization when it comes to Security Awareness or awareness. Creating unrest is never a good idea. Although you can also approach this with a positive mindset.
You can run an attack simulator , for example. This gives a realistic picture of the risk within your organization. You will quickly find that provided you have a low security-awareness you will have a relatively high score.
This fact gives you clout to start an initial safety program.
What is an attack simulator?
An attack simulator sends a fictitious e-mail to everyone in your organization. This e-mail will ask you to enter your username and password. Unfortunately, many people will leave their e-mail address and password without question.
Insurmountable, often. One person giving in to a phishing email can take an entire organization out of control. You can pretty well understand that if you have one account within an environment that you quickly make a lot of impact to access the next account to quietly evaluate to an account with multiple permissions. VPN access, or Office 365 administrator accounts. Domain administrator rights so full control. The new hacking is happening even from office 365 to on-premises.
An attack simulation is very easy to do. You can use this wizard to easily build an e-mail that you can distribute to the entire organization. You will be able to follow the score live in the reports provided. This can be set up and executed perfectly without IT knowledge. So the security cell or DPO can get to work with this.
Security Defaults for Microsoft 365 and Microsoft Azure
What is Azure AD Security Defaults
For Azure Active Directory. Office 365 and Azure's identity database, there recently exists a solution from Microsoft that integrates multiple security systems. 'Security Defaults'
Activating MFA, Conditional Access & blocking legacy
Security defaults is a single option that you can easily activate that performs multiple security implementations . The first security check is Multi-Factor Authentication. With Security Defaults , it is possible to turn on MFA and require all users to connect to Office 365 using the Authenticator App. Also, this default includes conditional access, (conditional Access) and blocking of legacy protocols . Such as IMAP, POP3. We all know this from the 2000s when we still had to use Skynet to configure our e-mail boxes.
You can activate Security defaults through this article.
Powerful safety considerations
In the first 30 days of activation of Office 365, Microsoft 365 or Microsoft Teams only, Microsoft strongly advises security recommendations to follow. Simple actions are:
- Basic administrator protections
- Logging activation and analysis
- Basic identity protection
- Tenant configuration
Microsoft SecureScore
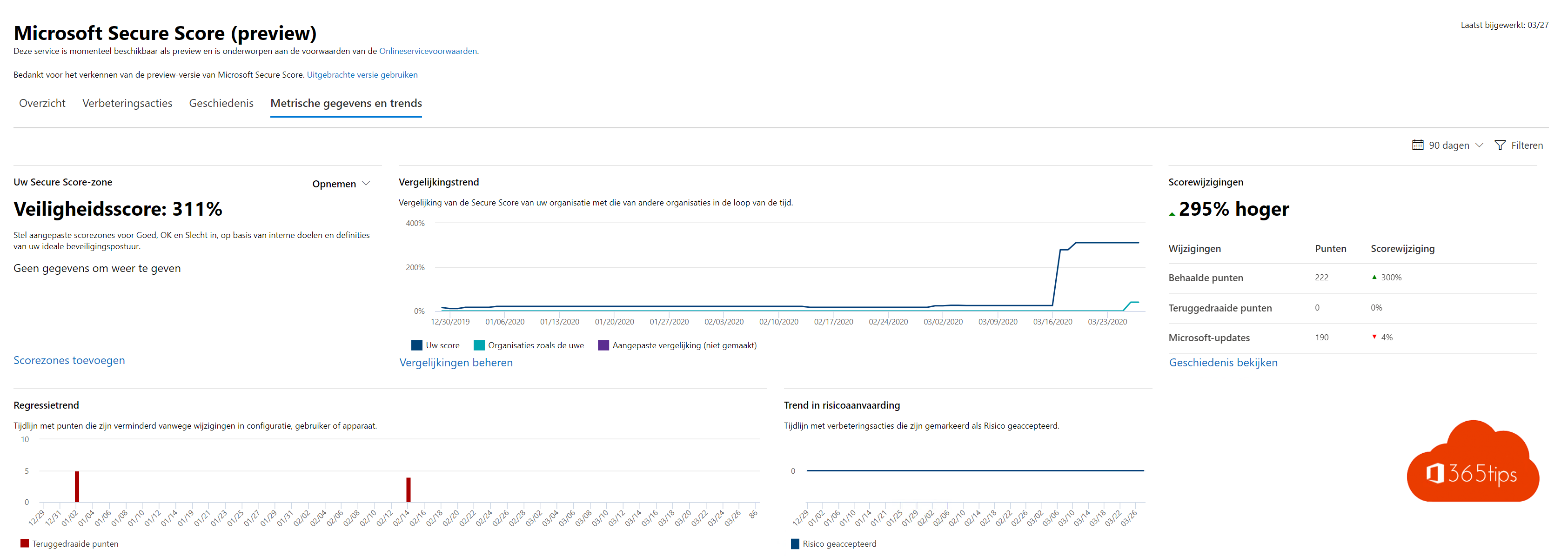
Microsoft Secure Score is a measurement of your organization's security. Where a higher number indicates that more improvement actions have been activated. Securescore is a service that not only covers the security configuration of your Office 365 environment, but also provides security recommendations to control and capabilities in other Microsoft services, including Azure AD under control.
Securescore general overview
- Security score for data, devices, applications and infrastructure.
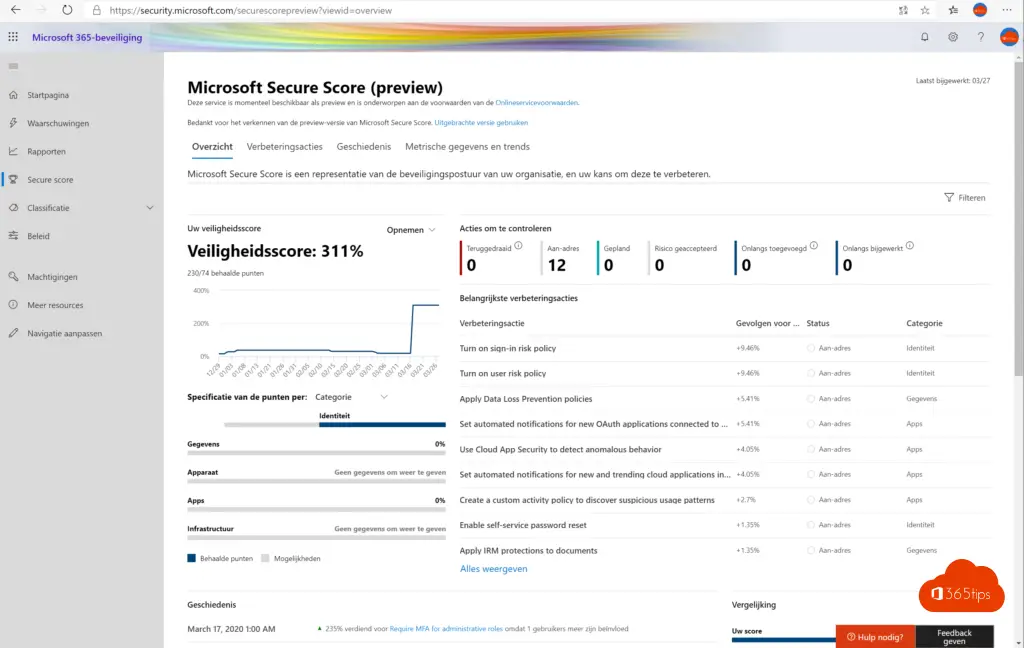
Accepted risk score
- Painful but 100% correct. If you have a score of 0% here you agree that you have not taken measures to secure your data from possible risks.
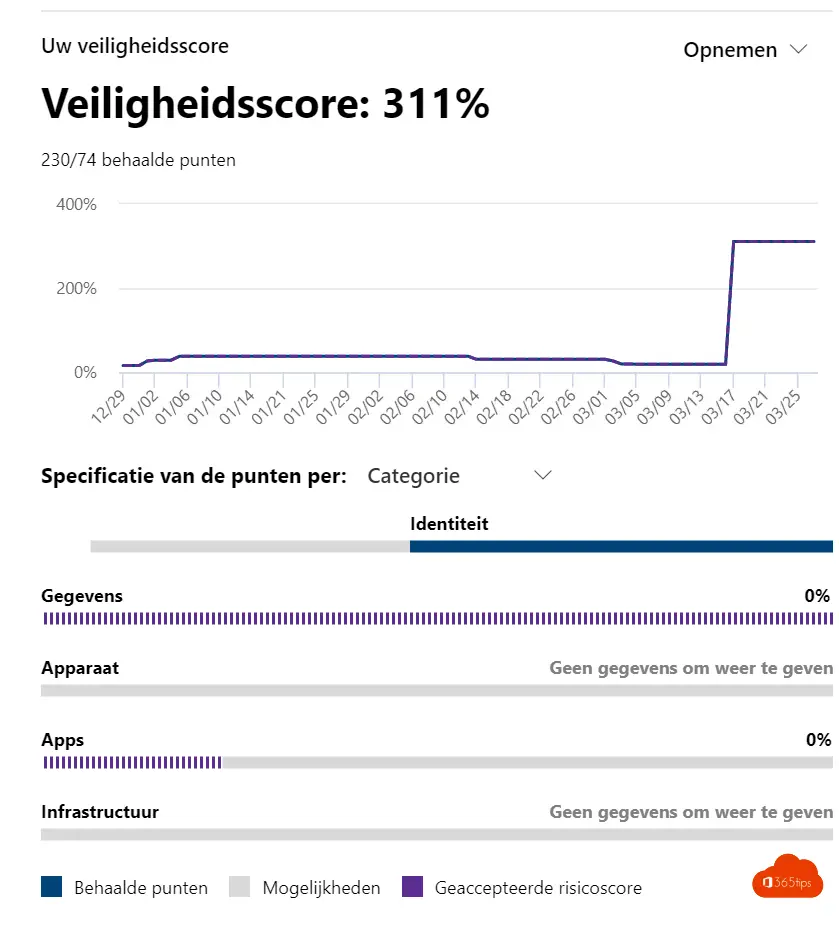
Improvement actions
- Improvement actions such as risk policies, as well as data loss prevention, self-service password reset.
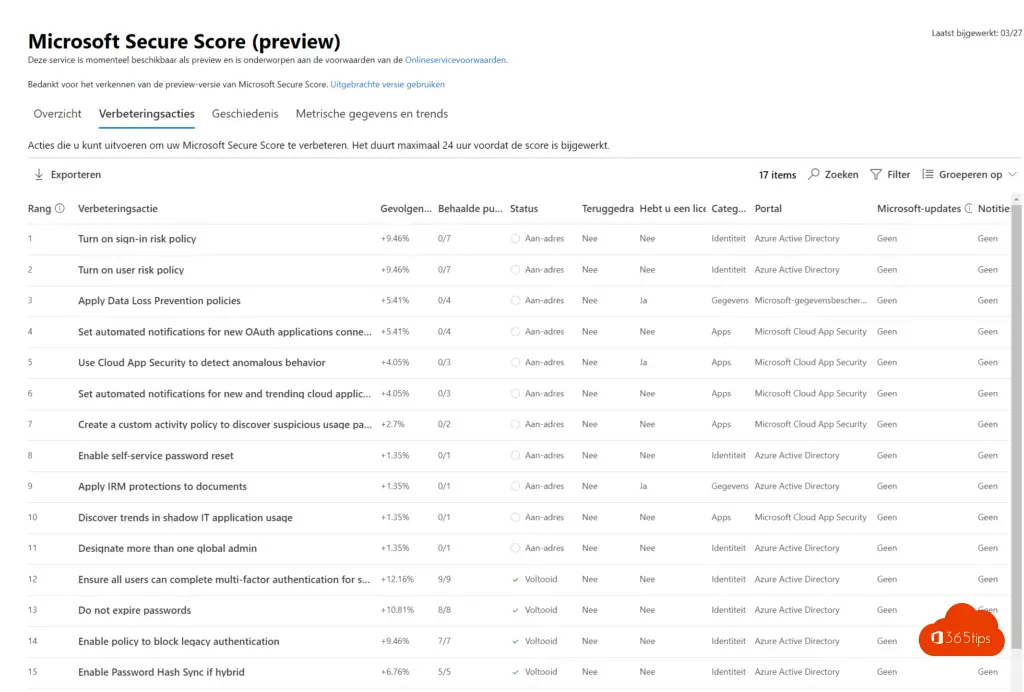
| Grade | Improvement action | Description |
| 1 | Turn on sign-in risk policy | Turning on the sign-in risk policy ensures that suspicious sign-ins are challenged for multi-factor authentication. |
| 2 | Turn on user risk policy | With the user risk policy turned on, Azure AD detects the probability that a user account has been compromised. As an administrator, you can configure a user risk conditional access policy to automatically respond to a specific user risk level. For example, you can block access to your resources or require a password change to get a user account back into a clean state. |
| 3 | Apply Data Loss Prevention policies | Data Loss Prevention (DLP) policies can be used to comply with business standards and industry regulations that mandate the protection of sensitive information to prevent accidental or malicious disclosure. DLP sends alerts after it scans for potentially sensitive data, such as social security and credit card numbers, in Exchange Online and SharePoint Online. Setting up DLP policies will let you identify, monitor, and automatically protect sensitive information. |
| 4 | Set automated notifications for new OAuth applications connected to your corporate environment | With app permission policies, you can discover Open Authorization (OAuth) abuse in the organization by identifying trending applications based on usage & permissions granted. |
| 5 | Use Cloud App Security to detect anomalous behavior | Cloud App Security anomaly detection policies provide User & Entity Behavior analytics (UEBA) and advanced threat detection across your cloud environment. |
| 6 | Set automated notifications for new and trending cloud applications in your organization | With Cloud Discovery policies, you can set alerts that notify you when new apps are detected within your organization. |
| 7 | Create a custom activity policy to discover suspicious usage patterns | Cloud App Security activity policies help you to detect risky behavior, violations, or suspicious data in your cloud environment. If necessary, you can also integrate remediation work flows. |
| 8 | Enable self-service password reset | With self-service password reset in Azure AD, users no longer need to engage helpdesk to reset passwords. This feature works well with Azure AD dynamically banned passwords, which prevents easily guessable passwords from being used. |
| 9 | Apply IRM protections to documents | Using Information Rights Management protections (IRM) on email and document data prevents accidental or malicious exposure of data outside of your organization. Attackers targeting specific, high value data assets are blocked from opening them without user credentials. |
| 10 | Discover trends in shadow IT application usage | Add a data source in automatic log upload for Cloud App Security Discovery to identify applications in your organization that run without official approval. After configuration, Cloud App Security Discovery will analyze firewall traffic logs to provide visibility into cloud applications' usage and security posture. |
| 11 | Designate more than one global admin | Having more than one global administrator helps if you are unable to fulfill the needs or obligations of your organization. It's important to have a delegate or an emergency account someone from your team can access if necessary. It also allows admins the ability to monitor each other for signs of a breach. |
| 12 | Ensure all users can complete multi-factor authentication for secure access | Multi-factor authentication (MFA) helps protect devices and data that are accessible to these users. Adding more authentication methods, such as the Microsoft Authenticator app or a phone number, increases the level of protection if one factor is compromised. |
| 13 | Do not expire passwords | Research has found that when periodic password resets are enforced, passwords become less secure. Users tend to pick a weaker password and vary it slightly for each reset. If a user creates a strong password (long, complex and without any pragmatic words present) it should remain just as strong in 60 days as it is today. It is Microsoft's official security position to not expire passwords periodically without a specific reason. |
| 14 | Enable policy to block legacy authentication | Blocking legacy authentication makes it harder for attackers to gain access. Office 2013 client apps support legacy authentication by default. Legacy means that they support either Microsoft Online Sign-in Assistant or basic authentication. In order for these clients to use modern authentication features, the Windows client has have registry keys set. |
| 15 | Enable Password Hash Sync if hybrid | Password hash synchronization is one of the sign-in methods used to accomplish hybrid identity. Azure AD Connect synchronizes a hash, of the hash, of a user's password from an on-premises Active Directory instance to a cloud-based Azure AD instance. Password hash synchronization helps by reducing the number of passwords your users need to maintain to just one. Enabling password hash synchronization also allows for leaked credential reporting. |
| 16 | Use limited administrative roles | Limited administrators are users who have more privileges than standard users, but not as many privileges as global admins. Leveraging limited administrator roles to perform required administrative work reduces the number of high value, high impact global admin role holders you have. Assigning users roles like Password Administrator or Exchange Online Administrator, instead of Global Administrator, reduces the likelihood of a global administrative privileged account being breached. |
| 17 | Require MFA for administrative roles | Requiring multi-factor authentication (MFA) for all administrative roles makes it harder for attackers to access accounts. Administrative roles have higher permissions than typical users. If any of those accounts are compromised, critical devices and data are open to attack. |
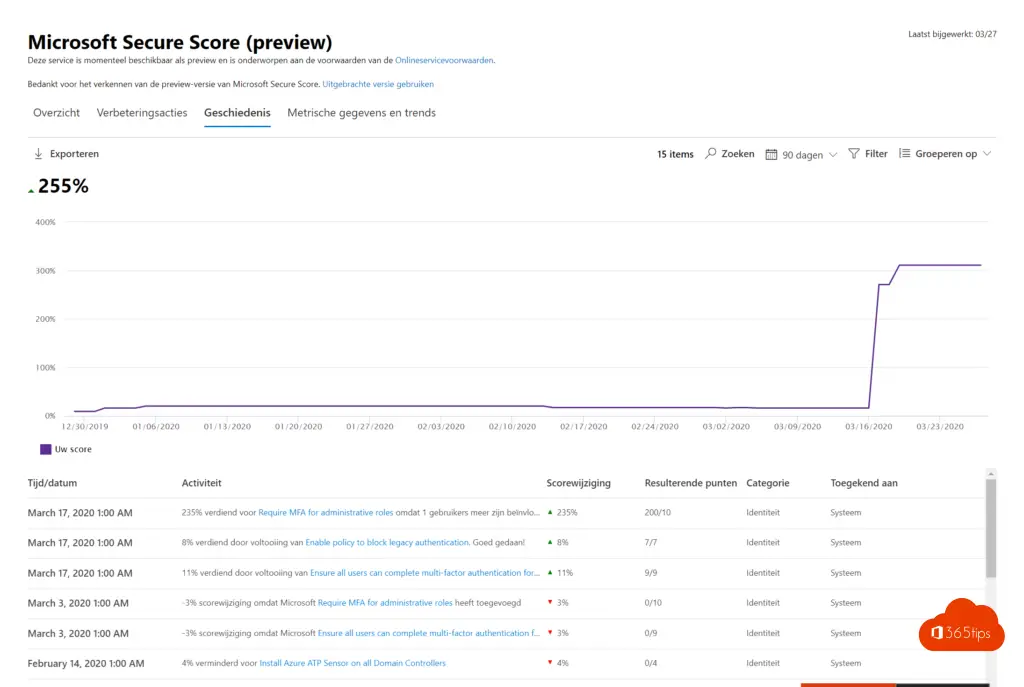
History
- In the history view you can see what actions you have already performed. Useful for reporting well on your organization's maturity score.
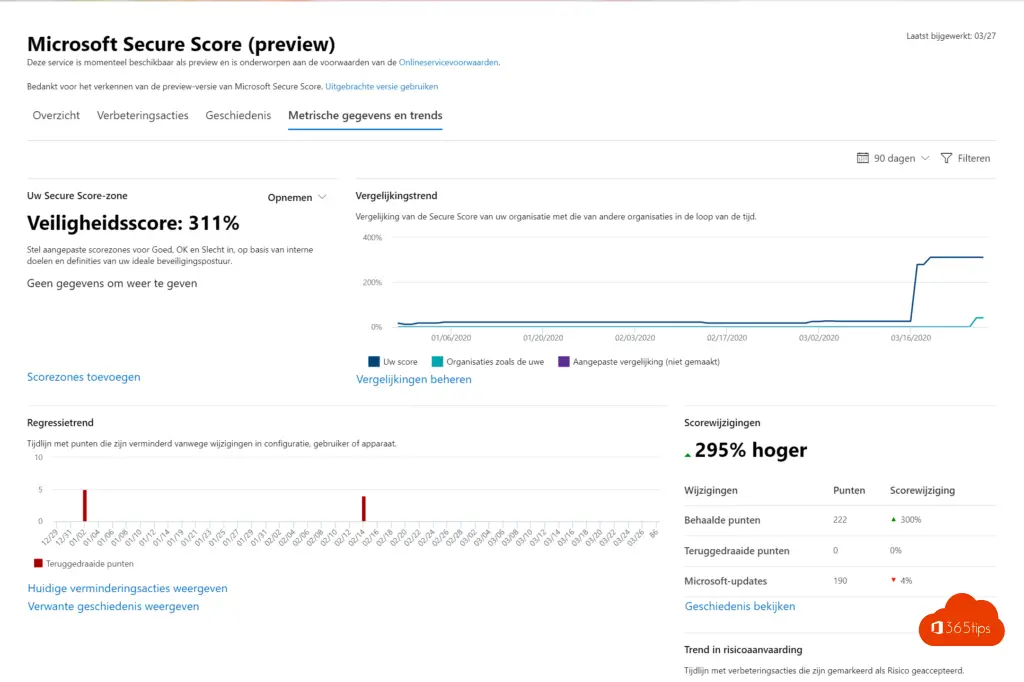
Metric data and trends
- Compare. Not really a great way to eliminate risk but a good median measurement.
Summary
Microsoft Secure Score is the perfect place to start to get security insights you can improve. Securescore shows the features, advice and security features that are activatable.
If there is still friction between the needs, one can work with: Awareness campaign within Office 365, but also the non-believer himself can check where he or she has logged in recently. Risky sign-ins is a third option that makes it very insightful to choose a more secure environment.
In the improvement actions, in this test-tenant you can find as many as 17 pieces of advice that are all realistic to implement.
Related blogs
Roadmap for securing Office 365 in the first 30, 60, 90 days
Check what location you logged into to make sure you weren't hacked
the 10 security recommendations we need to put in place now that we're working from home!
