Tutorial: Microsoft 365 security check for beginners!
Why is a Microsoft 365 security check so important?
- Office 365 has become an important platform since companies use it to share and store crucial information.
- We think Office 365 contains a fraction of the workshop but Office 365 is the fundamental building block for a future organization and often for today's organization.
- Thanks to Office 365 (broader Microsoft 365), there are huge insights into even your current on-premises environment.
- Emails: +90% of cybersecurity breaches start via phishing.
- Identity fraud. Did you know that your "technical" identity always comes from your on-premises infrastructure and is synchronized with Office 365.
- Specifically, this means that you have total visibility into your identity management. a huge measurement point that you can use to provide insight into your current infrastructure as well .
- The Microsoft 365 Security stacks is the help with cybersecurity!
What is best to write in a security assessment report?
Write a report with all the sensitivities you have seen thanks to the activation of the steps below. These topics are easy to take away. Write out the most important concrete recommendations. Build a priority list from most important to least important.
- Identity protection: leaked credentials. Which accounts are vulnerable? List these in one summary.
- Asset management: which devices are in management, which are not. Excel + chart.
- Mobile device management. What types of mobile devices are there. How are they managed + the difference between what we think and what we measure.
- Accounts with privileges. How many accounts with privileges, what privileges, etc..
- Is there active monitor.Has an effort been made to set up monitoring?
- Data protection. What is the current state of data-security.
- Is there an security awereness program. How to set this up in a few steps.
- Is there patch management of your your Windows but also your Mac systems. From your network devices, routers, switches to printers.
- Is a base security governance set up?
- What Microsoft 365 licenses does the organization have.
- Open security.microsoft.com or securescore.microsoft.com and list the most important implementations.
- Below you can find sample reports.
Start with a trial license of Microsoft 365 E5
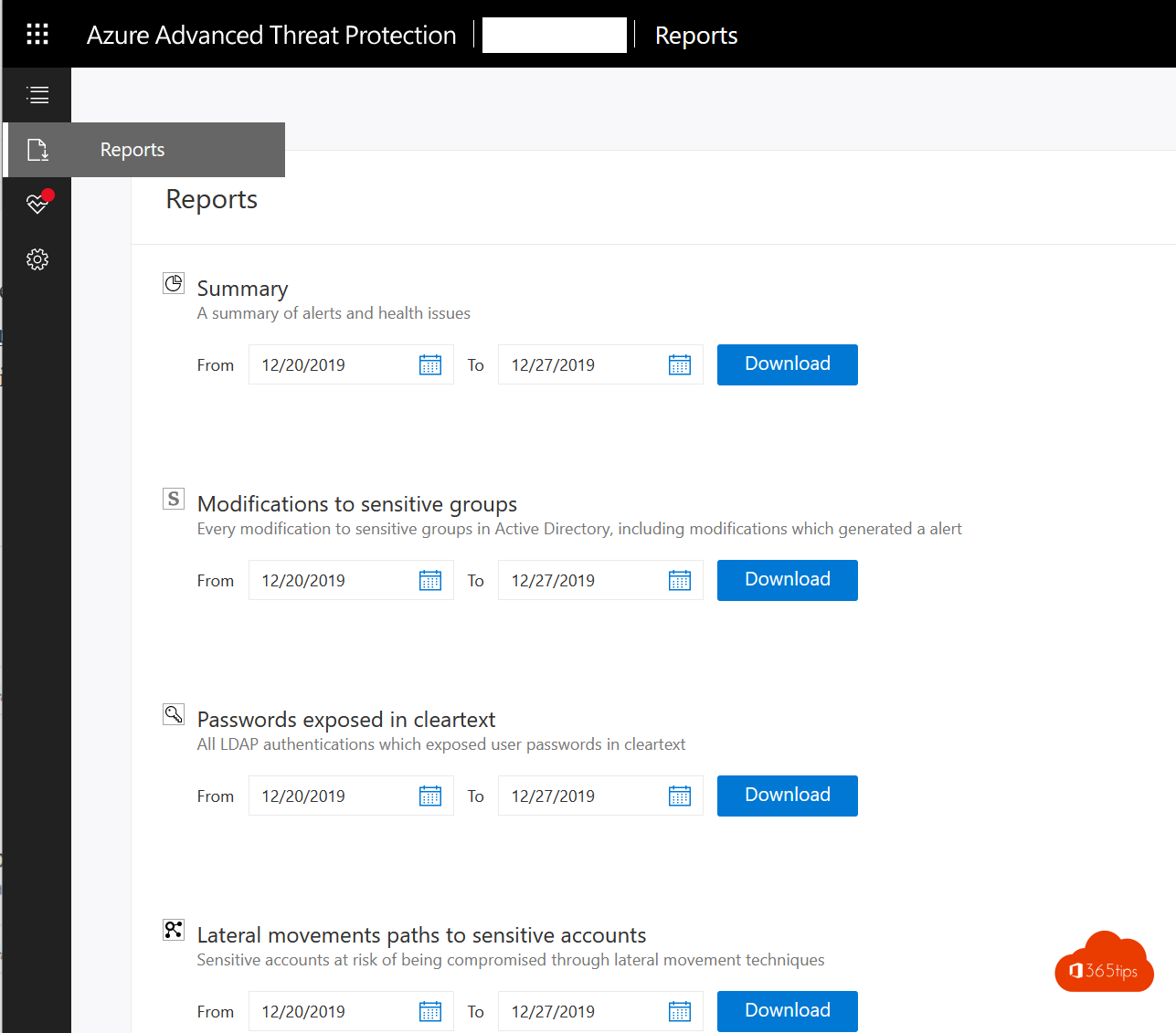
1. Install an ATP sensor on your domain controller(s).
Azure Advanced Threat Protection (ATP) is a cloud-based security solution that uses your local Active Directory alerts to identify, detect and investigate advanced threats, compromised identities and malicious insider actions targeting your organization.
With Azure ATP, SecOp analysts and security professionals can detect advanced attacks in hybrid environments!
- Microsoft has already explained how to do this in this article.
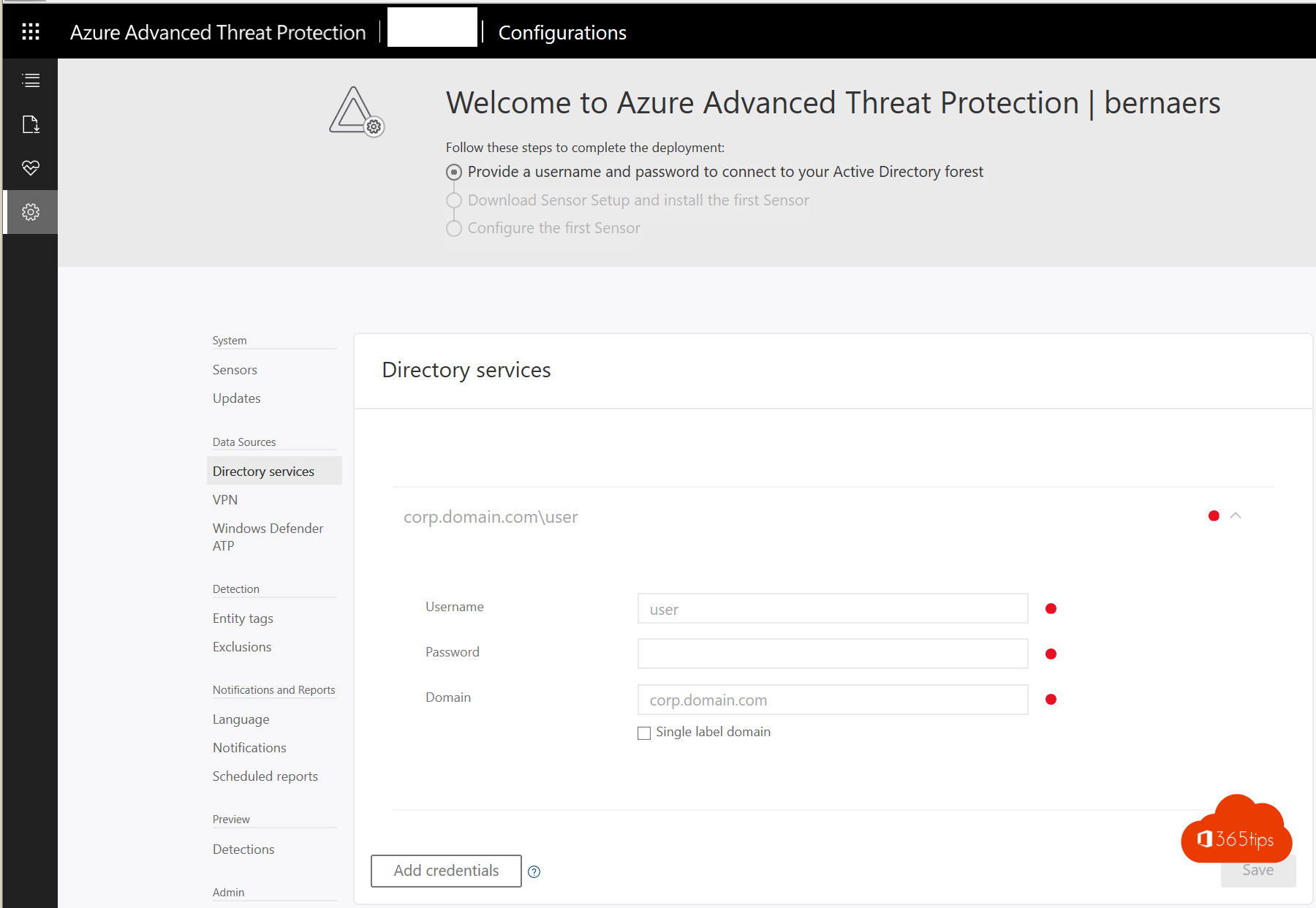
- Browse to https://portal.atp.azure.com
- Enter your credentials and press add-credentials at the bottom.
- Download the sensor and install it on your domain controller(s).
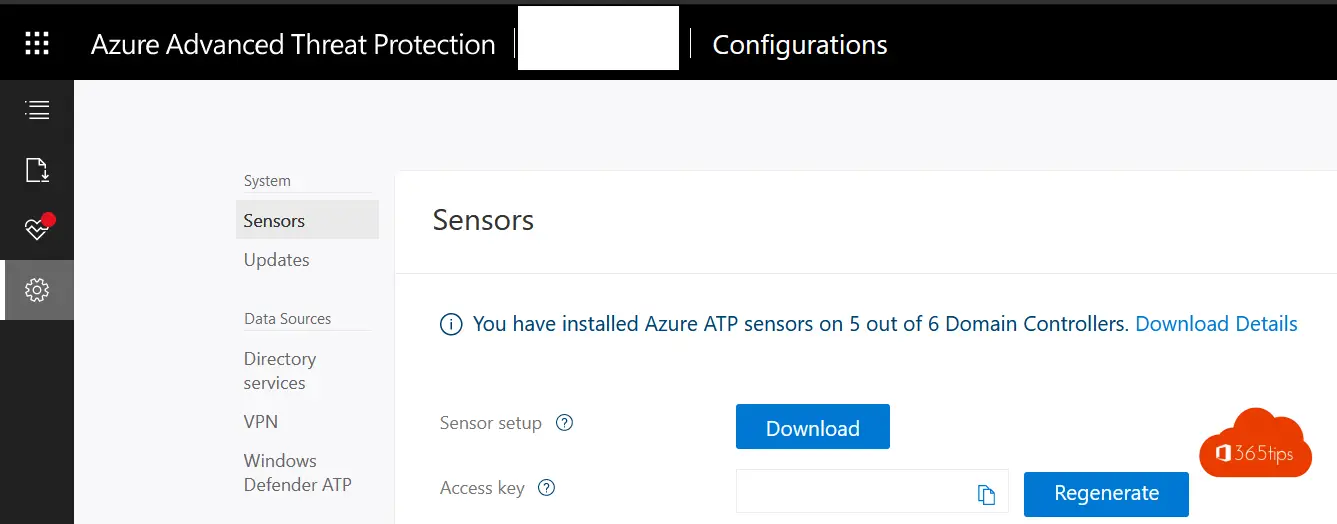
- From now on, logs on AD accounts will be shared with the Microsoft Security Stack.
With ATP, you can from now on:
- Finding passwords in clear-text in your area.
- Get lateral movement in a summary report.
- Seeing changes in sensitive AD groups.
- View an overview of your organization's health status.
Put these findings in your report!
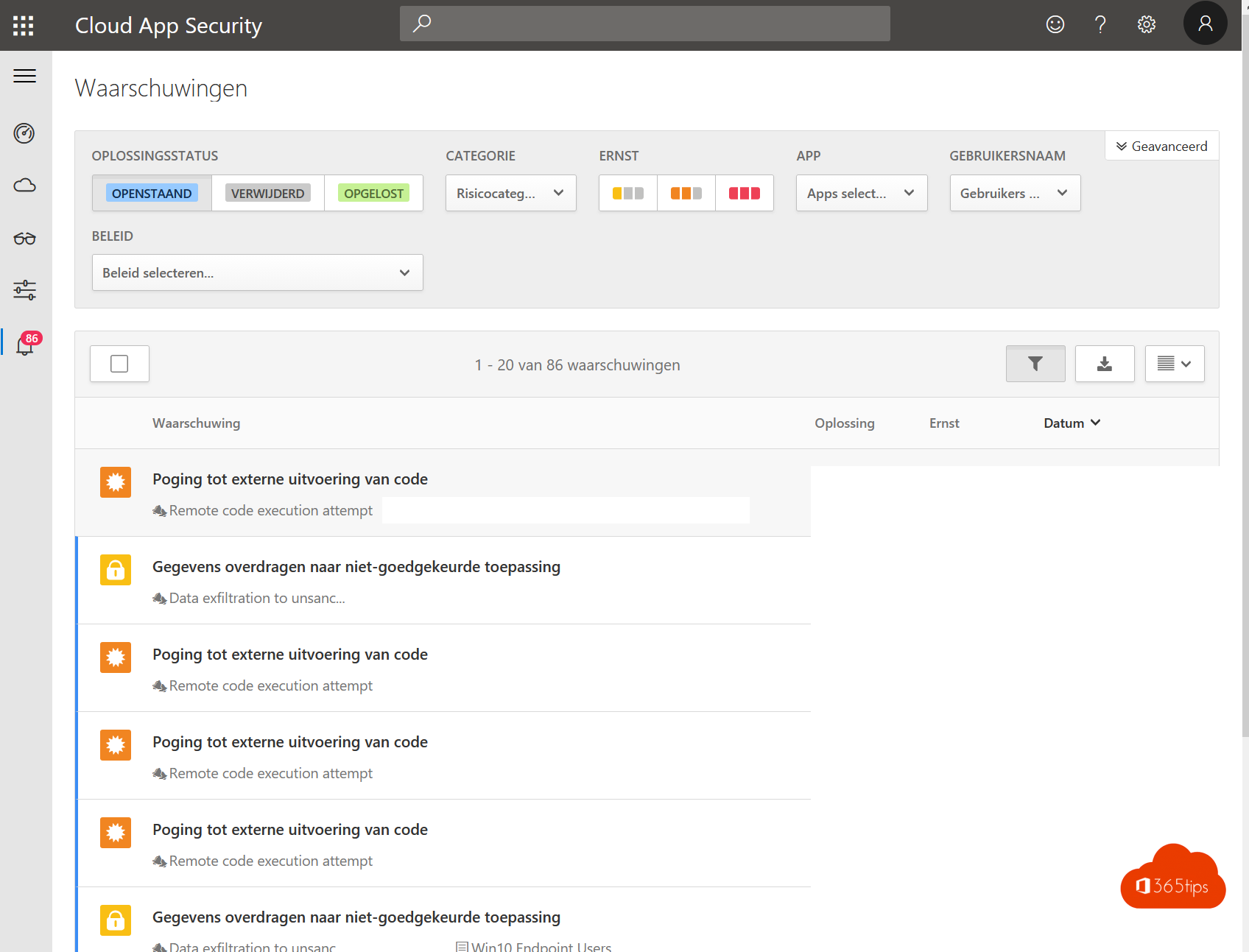
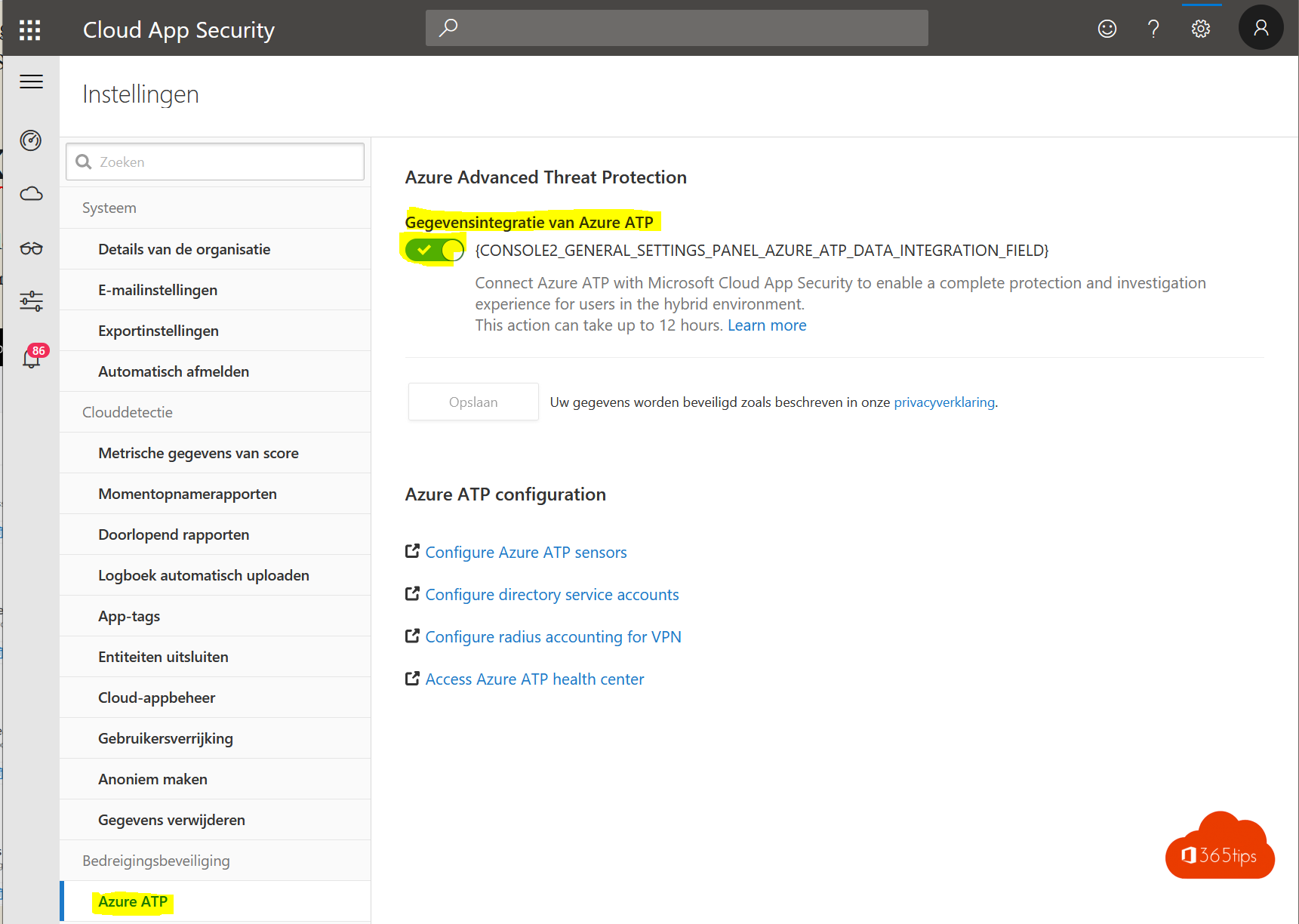
2. Cloud App Security
- Browse To: https://portal.cloudappsecurity.com/
- Using the wizard, create the CloudAppSecurity tenant Create. (Choose the region in which you wish to create your tenant ; West Europe)
- Connect Azure ATP to Cloud App Security via https://tenantname.portal.cloudappsecurity.com/#/settings?section=azureAtp (adjust your tenant name)
- From now on, your ATP data is contained in Microsoft Cloud App Security .
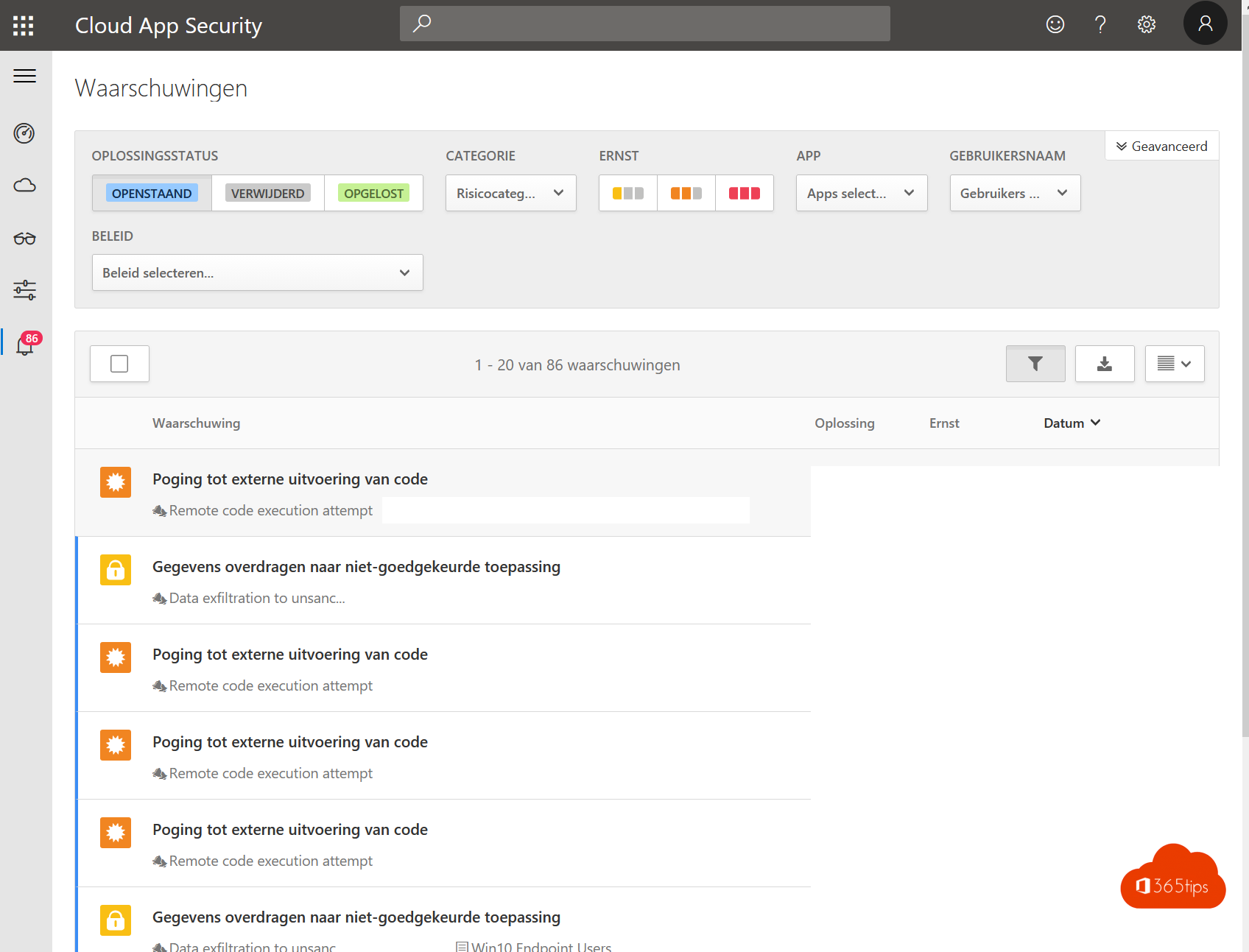
With Cloud App Security you now have:
- Insights into data leaks. (data exfiltration)
- Insights into leaked accounts, accounts used outside your geolocation in which you often work. (identity breaches, identity theft,...)
- Suggestions & tips to make your environment safer.
- Document insights & data export statuses. (Data exfiltration)
Turn off your stands https://portal.cloudappsecurity.com in your report!
3. Azure AD risky sign-ins
- Browse to https://po rtal.azure.com
- Navigate to Azure AD Risky Sign-Ins.
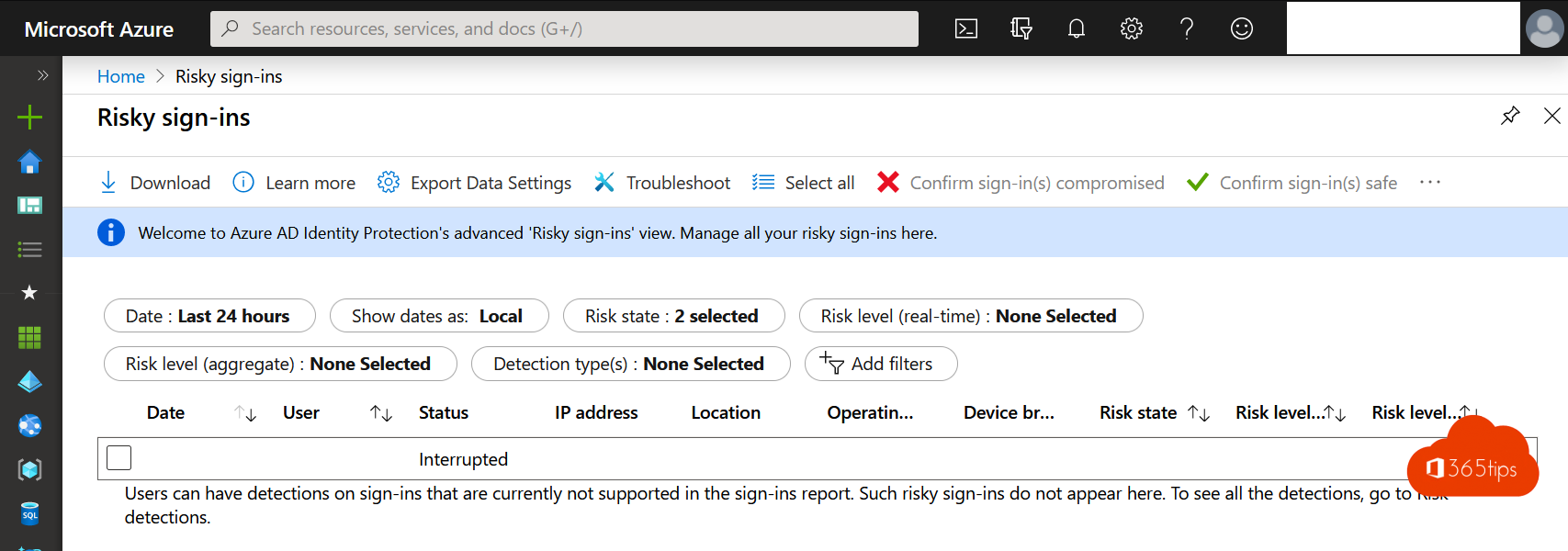
With Azure AD Risky sign-ins, you have insights into:
- The risks right now. Users logging in 500km from home while they were at the office last night. RISK!
- Concrete sugestions & recommendations.
4. Microsoft Compliance
- Since this has more of an impact on data security, we will include the detailed setup in a future blog.
- Through the compliance center, you can easily create labels of sensitive data, personal data and display them in your compliance dashboard. Easy! -> https://support.office.com/en- us/article/create-and-manage-sensitivity-labels-2fb96b54-7dd2-4f0c-ac8d-170790d4b8b9
- You can access the compliance center in advance at: https://compliance.microsoft.com/homepage
5. Microsoft's Security Center
- An important requirement is that you have WDATP/MDATP integrated on your devices.
- Microsoft Intune is not required, highly recommended.
- Microsoft Security Center gives you lots of insights around updates, security patches, spectre and meltdown and much more!
- Security center can be contacted at: https://securitycenter.windows.com/
- You'll read more in a subsequent blog!
Summary & conslusions
- The first 3 steps can easily be configured in one hour and provide tremendous real-time insights to improve your environment. This is best done in a pilot/test process. The other 2 require more work and are covered in subsequent blogs.
- These steps are the beginning to gain insights into your environment to make smart decisions OR dialogue for cybersecurity investments.
- Cross-platform. one cloud! Did you know you can also bring your on-premises infrastructure into this whole story to at least understand who and where is logging in and where your document data resides?
- The next steps, of course, are to gather even more insights. More integration, Active Directory assessments, policy review etc..
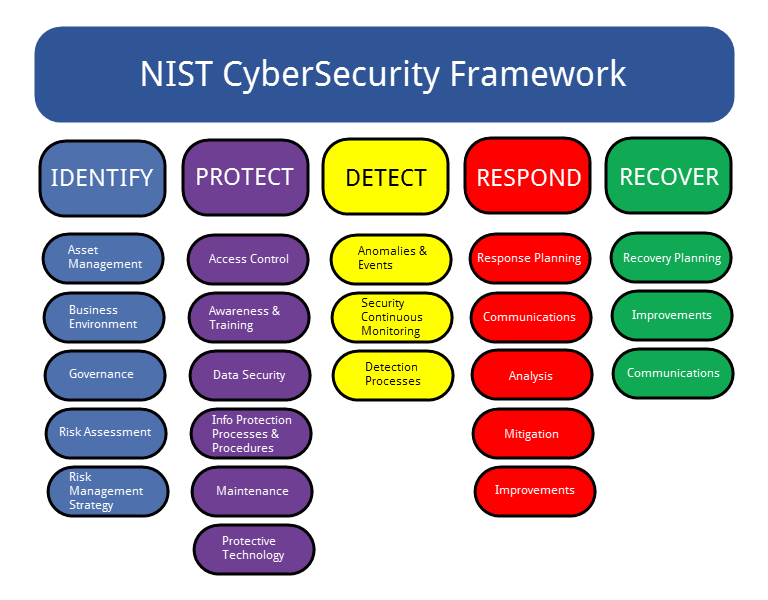
- a tip of the hat is to work with a framwork to take a structured approach to this. For example, NIST. In this you will work on the following 5 pillars to achieve a more secure environment. See also How to start with NIST.
- Other assessments obviously also exist such as: IT Risk Assessment, IT Audit, Red Team Assessment, Penetration Testing, Vulnerability Assessment....